IT resilience refers to a system’s ability to adapt swiftly to disruptions, ensuring continuous operations and minimal downtime. It’s crucial for businesses as it safeguards against financial losses, maintains customer trust, and sustains productivity in the face of IT failures or cyber-attacks.
Technicians coordinate in a control room with glowing screens and a world map display.
A recent cyberattack on July 19th involving CrowdStrike service disruption, which affected Microsoft services, underlines the necessity of cyber resilience in modern society.
This vulnerability can be seen as businesses depend more and more on their information technology system, and the risks associated with the possibility of cyberattacks or natural catastrophes are growing.
The CrowdStrike incident shows that even companies from the industry giants are vulnerable to disruptions, so organizations should pay much attention to IT business continuity.
CEOs and boards must understand that building IT resiliency has become obligatory rather than optional.
It is not just about adopting applications and reengineering processes—that is needed to create a sound plan to protect a business from adversity.
Business-critical applications and data must be protected, and the business has no choice but to invest in their protection for overall business resilience.
Based on occurrences like the CrowdStrike outage, companies should rely on protecting, enhancing, and developing their information technology structures.
This means cybersecurity must be strong and effective and constantly be on the global frontier of evolution and standardization.
Hi-tech technologies such as Artificial Intelligence or Machine learning make such risks more accessible to control, and companies can get ready to restore operations in the shortest time possible by utilizing advanced capabilities such as event correlation that can link data sets.
Most of the time, the fundamental principle when building resilience is to follow a good plan and conduct many tests.
Whichever way a business opts to have its IT architecture, whether using public clouds or pre-existing arrangements, its systems must be ready for anything.
The CrowdStrike outage should be a lesson for every organization that no company is immune to cyber threats—building up IT readiness is critical to preserving information, mitigating risks, and saving image and money in today’s world.
To address this issue and deal with surge volume, organizations should build infrastructure capabilities, such as containerized applications, to rapidly augment capacity across all components of the technical stack and address bottlenecks (such as message queues) in middleware.
Briefly recap the Microsoft-CrowdStrike outage and its global impact
On July 19, 2024, a large CrowdStrike outage affected millions of computers around the globe: more than 8. 5 million Windows systems.
As revealed by the insurers, this has caused average dollar losses for Fortune 500 companies to go a notch higher than five and a half billion dollars.
Some industries that have been greatly affected are the banking, healthcare, and airline industries.
The actual source of the problem was a malfunctioning test software that caused all sorts of issues for CrowdStrike, which promised to increase the company’s testing measures and deploy the changes over time to avoid such large-scale problems.
These insured damages are predicted to fall between 54-107 million and over 1 billion US dollars. As a result, CrowdStrike is providing the $10 Uber Eats as an act of good faith to the partners that have been impacted.
Key factors contributing to the severity of the outage:
1. Widespread adoption:
Endpoint security is criticized, including CrowdStrike, which has a large market share and has affected many systems.
Organizations across industries, governmental functionaries, core industries, including healthcare and energy, and banks and financial institutions that rely on endpoint security for their operations are thus severely vulnerable to loss of business when such security paradigms fail.
2. Dependency on cloud services:
Others depended on cloud interfaces such as Microsoft Azure and Google Compute Interface, all affected.
3. Rapid propagation:
The problem is exacerbated within the network’s transmits because of the update and the system’s boot mechanisms.
The importance of rigorous testing and quality assurance
It is also overemphasized that verifying everything and guaranteeing that the corresponding IT systems are strong and can recover from issues they face is crucial.
This means conducting tests and checks to detect defects not found before the software is released.
In quality assurance, people follow a specific protocol to facilitate the smooth operation of the software as designed and expected.
This means looking at the code, taking program modules and checking if they work independently, checking if they integrate well, and, lastly, trying to ensure a real user understands it well.
Emphasize the need for diverse IT solutions to mitigate risk.
It is advisable for firms not to centralize their operations and IT solutions because if a particular system becomes problematic, it will inconvenience the enterprise’s operations.
They should not rely on a single service or company for all the significant activities they carry out on the Internet.
Choosing more clouds, using different types of clouds, and selecting different companies for various components of their online environment – this way, businesses can avoid the mess when only one part fails, reducing the risk of single points of failure.
It should be noted that Gartner advises that organizations should pursue the multi-cloud approach as it helps to avoid total dependence on single points and thus choose the best environments for every specific task.
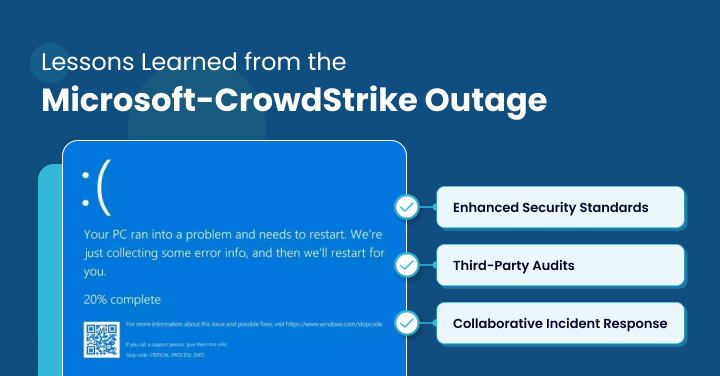
Lessons Learned from the Microsoft-CrowdStrike Outage
The Microsoft-CrowdStrike outage of 2024 provides several critical lessons for organizations:
Enhanced Security Standards: The incident highlights the need for stricter industry standards and security software development and testing regulations.
Third-Party Audits: Independent audits of security software can help identify potential vulnerabilities before they become critical issues.
Collaborative Incident Response: Fostering collaboration among security vendors and organizations can improve response times and knowledge-sharing.
Building a Resilient IT Infrastructure with Motadata
We offer a comprehensive suite of tools and solutions to make this possible. Our disaster recovery processes and services guarantee uptime and deliver measurable, trustworthy, and repeatable RPO and RTO (recovery point objectives and recovery time objectives) metrics.
When challenges arise, our disaster recovery plans are ready to swiftly get your systems back online, minimizing downtime and recovery time and keeping your operations running smoothly.
Data replication is at the heart of maintaining stability, and we ensure your critical information is safely copied and stored. This means that your data remains secure even if something goes wrong, and nothing is lost.
Our mission is to empower your IT operations to be resilient and prepared, equipped to face challenges head-on while safeguarding your most critical data. With the right tools, we ensure that your infrastructure is robust enough to withstand any obstacles and keep your business moving forward.
Motadata’s role in preventing or mitigating such outages
At Motadata, we take pride in playing a crucial role in preventing IT problems before they start and swiftly addressing them if they do arise. Our mission is to ensure that your IT systems are resilient enough to handle any challenge that comes their way.
We offer robust tools and services that empower companies to detect issues early on, preventing them from escalating into more significant problems.
In the event of a disruption, our disaster recovery and data replication solutions are designed to get everything back on track quickly, minimizing downtime and keeping your operations running smoothly.
Our comprehensive approach to IT resilience, including a solid backup and recovery strategy, means you can trust us to keep your services uninterrupted, even when the unexpected happens. We’re here to ensure your business stays strong, no matter what.
Explain how Motadata can provide early warning signs of potential issues.
Our advanced monitoring and analytics tools provide early warning signs, enabling businesses to address problems and maintain seamless operations proactively.
Comprehensive Monitoring and Data Analysis
Our platform continuously monitors critical components of your IT ecosystem, including infrastructure, applications, and key assets.
Collecting and analyzing vast amounts of data in real time, we identify anomalies and irregularities that could indicate underlying issues.
For instance, our solution tracks CPU utilization, memory usage, and network latency across all devices and applications.
When any parameter deviates from its normal range, the system triggers alerts, allowing your team to investigate and resolve issues before they impact performance.
Predictive Analytics and Machine Learning
Motadata leverages historical data through predictive analytics. We analyze past patterns Using machine learning algorithms to forecast potential disruptions.
For example, our system might detect a trend of increasing disk space usage over time, signaling capacity planning needs before storage runs out.
Similarly, by analyzing workloads and resource utilization, Motadata can predict potential bottlenecks and recommend load balancing or workload redistribution to prevent system crashes.
Automated Response and Recommendations
When our system detects a potential problem, it can automatically trigger predefined runbooks or workflows to address the issue.
For instance, if a server shows signs of overheating, Motadata can initiate a cooling procedure or redistribute the workload to prevent a shutdown.
Additionally, our platform offers recommendations based on data-driven insights, advising on actions such as scaling resources, applying patches, or optimizing configurations to ensure long-term stability.
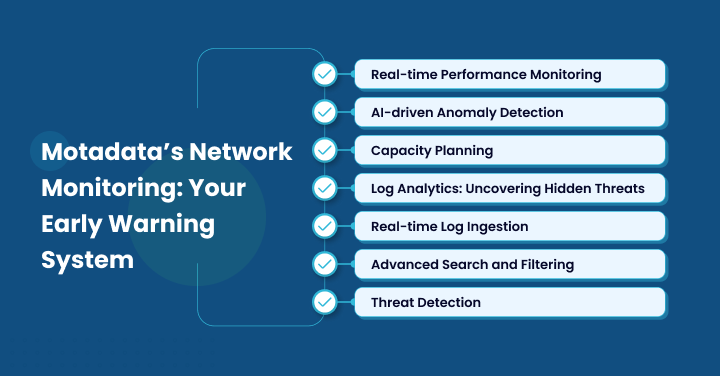
Motadata’s Network Monitoring: Your Early Warning System
Our network monitoring solution serves as your early alert system, ensuring that your IT infrastructure stays up and running smoothly.
We keep a vigilant eye on your network 24/7, allowing you to spot and resolve issues before they escalate and impact your business operations.
By providing a clear view of everything happening within your network, we enable you to monitor data flow, system performance, and any potential bottlenecks or delays that could disrupt your operations.
Understanding what’s normal for your network allows us to quickly identify any anomalies that might indicate potential threats or issues. With this early warning system in place, you can take immediate action to prevent downtime and maintain optimal performance.
Real-Time Performance Monitoring
We understand the importance of real-time monitoring in building IT resilience and avoiding disruptions to your internet or applications.
Our system continuously monitors the critical components of your network, including servers and applications, allowing us to detect and address issues as they arise.
With our real-time performance monitoring, we provide insights into data transfer speeds, packet loss, bandwidth usage, and other key metrics.
By closely monitoring these details, we can identify and address potential problems before they significantly impact your network’s performance.
This proactive approach helps you pinpoint bottlenecks and keep your operations running smoothly.
AI-Driven Anomaly Detection
We leverage AI to detect unusual activity within your network, which is crucial for identifying threats and performance issues early.
Our intelligent algorithms analyze vast amounts of data related to network behavior, device activity, and user interactions. This allows us to establish a baseline of what’s normal and flag any deviations that could indicate trouble.
By utilizing AI-driven anomaly detection, we empower you to respond swiftly to emerging issues, preventing them from escalating into major problems.
Our technology doesn’t just react to issues as they occur; it also predicts potential problems. By analyzing historical data and trends, we can alert you to potential future challenges, ensuring that you’re always prepared.
Capacity Planning
Regarding capacity planning, we analyze network traffic, server load, and storage utilization to help you predict future needs and allocate resources more effectively. By examining trends and patterns in your data, we enable you to anticipate demand and optimize your IT infrastructure accordingly.
Our tools make it easier for you to build IT resilience and dynamically manage workloads. We help you adjust resource allocation based on real-time demand, ensuring seamless performance without slowdowns.
Our holistic approach simplifies workload mobility and capacity planning, allowing you to easily protect, recover, and move applications across hybrid and multi-cloud environments with agility.
This approach ensures that your IT backbone remains strong and agile, ready to handle any challenges that come your way.
Log Analytics: Uncovering Hidden Threats
In today’s cybersecurity landscape, identifying hidden threats is paramount.
Our log analytics capabilities empower organizations to detect these dangers swiftly by analyzing logs from various sources, including network devices, servers, and applications.
Through this process, we gather, categorize, and examine log data to uncover unusual patterns or indicators of potential security issues.
By correlating this data with up-to-date threat intelligence, we can alert organizations to risks they may face, enabling them to take proactive measures.
Real-Time Log Ingestion
We ensure businesses have immediate access to their log data by facilitating real-time log ingestion.
As logs are generated across different environments, whether from network devices, servers, or applications, we capture and analyze them on the fly.
This continuous stream of information provides a dynamic and accurate overview of the IT landscape as events unfold.
With this real-time insight, organizations are always aware of the state of their IT systems, allowing them to act quickly if something appears suspicious.
By processing logs instantaneously, we enable rapid detection and investigation of any anomalies as they occur, bolstering the organization’s ability to respond to potential security threats.
Advanced Search and Filtering
Navigating through vast amounts of log data can be daunting, but we simplify this process with advanced search and filtering capabilities.
Our sophisticated search functions allow users to define specific criteria such as timeframes, source locations, severity levels, and key terms, making pinpointing critical information within the logs easier.
When a security incident or operational issue arises, these targeted searches help organizations swiftly uncover the root cause.
Additionally, our filtering tools enable further refinement by narrowing the focus to specific log sources or events, ensuring that users can quickly extract valuable insights without being overwhelmed by irrelevant data.
Threat Detection
Our threat detection features are designed to help businesses identify and address security risks in real-time.
By meticulously analyzing logs and cross-referencing them against known threat indicators, we provide timely warnings about potential security breaches as they emerge.
This detection process hinges on identifying anomalous patterns or behaviors within the log data, which may signal vulnerabilities or malicious activities.
We continuously adapt to detect new and evolving threats by leveraging advanced technologies like machine learning.
This constant vigilance ensures that organizations maintain robust defenses against an ever-changing array of cyber threats, helping them avoid potential risks.
Network Automation: Accelerating Incident Response
Motadata’s network automation speeds up businesses’ reaction times to problems, helping them fix things faster. By making repetitive tasks and workflows automatic, there’s less need for people to step in, and incident fixing times are shorter.
With network automation, the system automatically finds, diagnoses, and fixes network issues.
Thanks to our AI-driven algorithms, our system can spot when something isn’t right on its own, alert you about it, and start taking steps to make things better without needing someone to tell you what to do.
The cool part is that these systems can also fix themselves in many cases. If something goes wrong, they’re designed with self-healing abilities, which means they try their best to identify and recover from faults by themselves.
By implementing Site Reliability Engineering (SRE) processes and technologies, businesses can achieve high service availability and ensure their networks stay strong no matter what happens.
On top of all that good stuff, Motadata makes sure its solution works well with other tools your business might be using, allowing everything involved in handling incidents to become smoother across your entire IT ecosystem
Self-healing capabilities
We offers a network automation solution that comes with self-healing features.
This means it can fix problems independently, keeping the network running without needing people to intervene. Companies can make their networks more reliable through smart algorithms and automation without doing much.
What is IT resilience, and why is it important for businesses?
With these self-healing features, any issues in the network are quickly spotted and fixed immediately. This helps keep everything running smoothly, reducing pauses or breaks in service. It’s all about catching problems early so businesses don’t have to deal with interruptions.
In addition, if something goes wrong or there’s a hiccup in the system, Motadata’s technology knows how to handle it by moving data around or using different resources.
This way, critical applications stay online no matter what happens, which is key for keeping things going even when there are bumps along the road.
In short, resilience, less downtime, and fewer disruptions come from using Motadata’s tools because they automate processes that used to need human hands-on work.
Integration with other tools
Motadata’s network automation solution works well with other tools and platforms. This integration helps businesses improve their incident response and how their whole IT ecosystem functions.
By combining it with the IT infrastructure and applications a company already uses, companies can get more out of what they have and work more efficiently on a single platform.
With these integration features, companies can centralize all their incident management tasks, share data automatically between different systems, and help teams work better together.
By combining all this information and workflow, companies can reduce the need to do the same thing more than once and ensure everyone responds to incidents similarly.
Also, because Motadata’s solution fits nicely with other tools a business might use, everything will work smoothly together without hiccups. This lets businesses keep using what they’ve invested in while strengthening their IT setup.
Service Desk Excellence: Keeping Your Users Informed
Motadata looks at making IT tough and reliable, focusing on having an awesome service desk that ensures problems are fixed fast and customers are happy. They offer a strong service desk tool to help businesses keep everyone updated, sort out issues quickly, and improve users’ experiences.
Having a top-notch service desk means implementing the best ways to deal with incidents, solve problems, and adhere to ITIL rules. Companies can deliver steady and effective services by keeping all incident reports in one place to be tracked and sorted out efficiently.
When handling incidents well, it’s all about logging them as they come in, figuring out which ones need immediate attention, and resolving them without wasting time.
This reduces any stoppages or interruptions in work. Keeping users looped in on what’s happening with their issues also goes a long way toward making customers feel valued and maintaining great user experiences.
Through Motadata’s focus on excellent service desks, businesses can manage incidents effectively, increase customer happiness, and ensure their IT operations stay resilient against challenges.
Incident and problem management
Motadata’s service desk is skilled at handling issues and problems to keep IT operations running smoothly. They use the best methods for dealing with incidents and solving problems so businesses can continue without much trouble.
With incident management, they find, sort out, and fix any issues quickly. By sticking to ITIL rules and using automation, companies can make their process of managing incidents more efficient and provide reliable services all the time.
Problem management is all about figuring out why certain issues keep happening. By identifying these problems and taking steps to prevent them from occurring again, companies can reduce the frequency of these issues, strengthening their IT operations overall.
Knowledge base
In the world of IT, keeping things running smoothly is key. Motadata tells us that having a sound system for managing what we know – think of it as a giant library of info – helps make our IT work stronger and more bulletproof.
This big library, or knowledge base, keeps all sorts of helpful stuff in one place: like tips on how to do things better (best practices), step-by-step guides for fixing problems (troubleshooting guides), and general advice on making sure everything works well together (standard procedures).
With this setup, the IT team can find what they need quickly and work together more effectively.
This means when something goes wrong, they can fix it faster; plus, they get better at solving new problems over time.
Motadata has some smart tools that help businesses build up their knowledge bases to keep track of all these helpful insights and experiences, making them more challenging against any tech troubles – boosting their resilience in the long run.
ITIL compliance
Following ITIL (IT Infrastructure Library) rules is key to strengthening IT systems.
It’s like a guidebook for managing IT services so they match up with what the business needs.
Motadata has created solutions that stick to these important standards, helping companies use well-known methods and steps.
Sticking to ITIL means making sure that IT services are given out smoothly, work well, and always get better.
Using what ITIL suggests, businesses can better handle their infrastructure and services, reduce times when things aren’t working right, and make everything run more smoothly.
With tools from Motadata designed for this purpose, organizations have what they need to meet these standards head-on, which helps them keep delivering strong services even when unexpected problems arise.
IT Asset Management: Knowing Your Inventory
Managing IT assets effectively is essential for maintaining operational continuity and efficiency.
Our approach ensures comprehensive tracking and management of critical IT assets, from hardware like servers and desktops to software, including customer relationship management systems.
This holistic management strategy begins with a complete inventory of assets, encompassing software licenses, hardware performance monitoring, and timely maintenance or upgrades.
By staying vigilant about our IT assets, we optimize resource utilization, reduce long-term costs, and prevent disruptions caused by outdated or unsupported technology.
This clarity in it asset management strengthens our operational resilience and ensures we are always prepared for the demands of the business environment.
Software License Management
Handling software licenses with precision is vital for legal compliance and operational efficiency.
We understand the importance of meticulous license management, ensuring that all software usage is within the bounds of legal agreements, thereby avoiding penalties and preventing workflow interruptions.
We maintain compliance effortlessly by utilizing advanced tools to manage licenses and ensure optimal software utilization.
This proactive approach to license management safeguards against legal risks, keeping operations seamless and enhancing our overall system resilience and business continuity.
Comprehensive Asset Discovery
Accurately identifying and monitoring all IT assets is crucial for effective management and operational efficiency.
We prioritize a thorough discovery process to catalog every hardware and software within our network.
We maintain a detailed and up-to-date inventory through automated network scans, enabling us to manage assets more efficiently and monitor their performance effectively.
This comprehensive visibility into our IT environment ensures critical applications remain reliable, accessible, and secure.
By leveraging advanced tools for automatic tracking, we eliminate the need for manual audits, streamline asset management, and reinforce our systems against potential disruptions.
Patch Management: Staying Ahead of Vulnerabilities
Effective patch management is essential for safeguarding IT systems against vulnerabilities.
Our strategy emphasizes proactive identification, assessment, and application of security patches to address potential weaknesses and stabilize our infrastructure.
By staying current with patch management, we mitigate the risk of security breaches and ensure the continuous smooth operation of critical applications.
Our automated approach to patch management allows us to swiftly deploy updates, ensuring compliance with security standards and enhancing the resilience of our IT backbone against emerging threats.
Vulnerability Assessment
Regular vulnerability assessments are crucial for maintaining system integrity and security. We recognize the importance of continuously scanning our systems for weaknesses, allowing us to address potential security gaps before they can be exploited.
This proactive approach identifies areas where security measures may be insufficient, enabling us to strengthen our defenses before any potential attacks.
By utilizing automated tools for vulnerability assessment, we prioritize and remediate risks promptly, fortifying our IT infrastructure and reducing the likelihood of security incidents.
Automated Patch Deployment
Automated patch deployment is integral to maintaining the security and stability of our IT systems.
We highlight the significance of automating the patching process to ensure the timely application of security updates, which is critical for protecting against vulnerabilities and maintaining system performance.
Manual patching can be time-consuming and error-prone, increasing the risk of security breaches or operational failures.
By embracing automation, we expedite the deployment of patches, securing our critical applications and minimizing exposure to potential threats.
This approach ensures our systems remain up-to-date and protected, safeguarding our operations from unforeseen vulnerabilities.
Conclusion
Wrapping things up and keeping your IT infrastructure safe from any possible problems in today’s world, where everything is online, is super important.
Motadata has this whole plan that uses the latest tech, like AI and machine learning, to spot and stop dangers before they happen.
They use top-notch data protection methods and tools to monitor networks so you get a heads-up if something seems off, helping you keep your IT setup tough against troubles.
With Motadata, you can count on smooth network automation, smart log checking out, great help desk support, managing IT stuff well, and ensuring everything’s updated to fight weak spots.
Stay one step ahead of what could go wrong with Motadata’s solid plan for keeping your IT strong.
FAQs:
Motadata taps into cutting-edge techs like AI, machine learning, and anomaly detection to spot and stop possible IT dangers.
By keeping an eye on the it infrastructure non-stop and studying how data behaves to pick up on anything unusual or any signs of a security issue, this platform is always one step ahead.
With its automated systems and instant notifications, Motadata equips companies with the tools they need to avoid IT threats, reducing the chance of any interruptions in their operations.
Motadata shines compared to other IT resilience tools because it has something special that sets it apart.
With its advanced capabilities, the platform easily meshes with what businesses already have in place for their IT infrastructure and offers all-around support.
This mix of qualities helps companies boost their resilience, ensuring that important applications and data are secure and always available.
Motadata’s solutions fit perfectly with your existing IT infrastructure. Their platform ensures it will work well with different systems and applications, so moving to it is easy and won’t cause headaches.
It also lets businesses make the most of what they’ve already invested in, boosting their IT resilience simultaneously. Motadata’s scalable solutions can grow with you as your business grows and changes, meeting your future IT needs without a hitch.