Hybrid cloud services have become a cornerstone for many businesses. These technologies, which combine the strengths of private and public clouds, assist enterprises in achieving their dreams of scalability, flexibility, and cost-efficiency.
However, this added optimization comes at a cost, particularly with increased operational complexity and security concerns.
To minimize cyber threats and secure their data, businesses must invest in more security solutions, such as log monitoring. This is a proactive measure to detect, analyze, and respond to potential threats within the company’s system.
Unfortunately, like any other integration, using log monitoring safely requires companies to understand how the solution works and its potential challenges.
This article discusses how long monitoring is essential in securing hybrid cloud infrastructure and optimizing operations. It also outlines how companies can implement the solution to tackle emerging security and performance issues.
What is Log Monitoring?
It collects and analyzes logs from various servers, applications, and other infrastructure components. Logs are digital records of user activities and security incidents within the business’s environment.
The primary role of log monitoring is to detect, prevent, and resolve any issues that may arise within the network, regardless of size.
Log monitoring tools often use technologies like automation, machine learning, and artificial intelligence to process massive amounts of data. This makes it vital for modern IT experts to identify and prevent security threats within the system.
Software developers can also use these activity monitoring solutions to add ingest systems, applications, and service logs to the organization’s network. This helps them to quickly identify problems at any point of the software delivery lifecycle (SDLC).
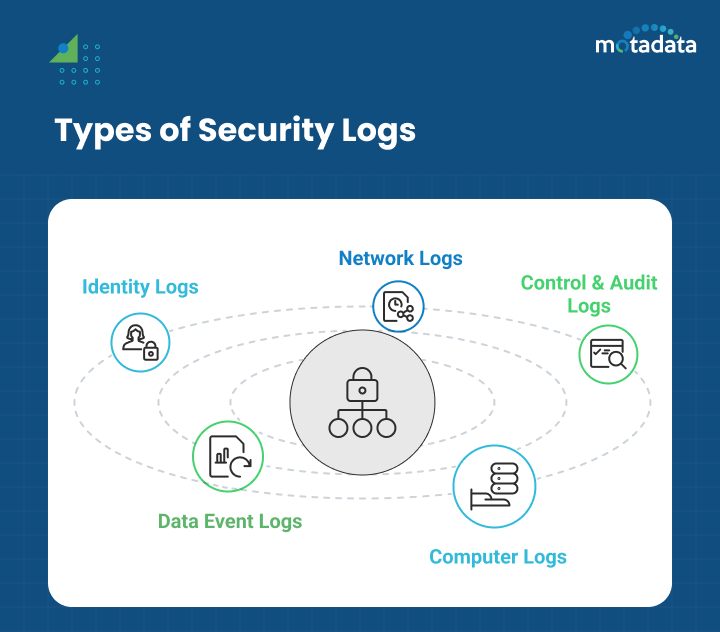
Types of Security Logs
Log monitoring works by documenting all the system activities. However, to achieve comprehensive protection from internal and external threats, it is essential to identify specific log sources.
Here are the common log categories to help organizations create effective measures to mitigate risks.
Identity Logs
These logs track and register all user verification activities. They record login attempts, password changes, and user privilege escalations. Their primary components include timestamp registration, IPs, verification types, and unauthorized access attempt feedback.
Identity logs provide a comprehensive analysis of user behavioral patterns and anomalies. Some logs will even record risks based on severity and send critical threats to security teams for more investigation.
For example, a continuous record of unauthorized access from a particular ID or location could signal a potential brute-force attack. Assigning a risk score to this attack forces the system to act quickly and prevent further risks.
Network Logs
These capture information about data traffic and communication between systems. In other words, they provide a detailed analysis of the amount of data transferred, their sources, destination, and protocols used. IT experts can use this information to effectively detect traffic patterns and stop potential threats before they occur.
Network logs enhance breach prevention, system performance, and seamless cloud operation. Combining them with other attack detection tools enables companies to efficiently identify and stop fraudulent actions. This includes preventing risky threats such as Distributed Denial of Service (DDoS) attacks.
Control and Audit Logs
These logs track system or configuration changes and administrative actions. They focus on what, who, when, and how changes were made.
They also record policy updates, permission changes, and new service deployments. Key elements in the logs include user IDs, change descriptions, timestamps, and affected resources.
Control and audit logs are essential in ensuring the organization meets regulatory requirements by providing detailed administrative records.
They also support proactive security measures by recording deviations, enforcing security policies, and enabling real-time alerts for suspicious activities.
Integrating them with other cloud monitoring services gives security teams a unified analysis of administrative actions performed across the system.
Data Event Logs
These record all events related to data access, modification, and deletion. They provide information like who accessed the data, when, how much, and where data was accessed. Their main components include user IDs, data object IDs, types of operations performed, timestamps, and the source IP.
Data events logs are essential in maintaining the company’s cyber security integrity by providing a detailed audit of each action. This ensures transparency within the system, reducing the company’s exposure to attacks. For example, many files downloaded by a single user could indicate potential internal threats.
Computer Logs
Compute logs track the performance and operations of virtual machines, containers, and serverless functions within the infrastructure. They detail CPU and memory usage, start and stop log entries, scaling activities, and error messages. Their key elements include instance IDs, resource usage metrics, timestamps, and event types.
Combining compute logs with other host technologies yields several advantages to organizations. These include enhancing performance optimization by adjusting resource allocation.
For instance, by monitoring container platforms, the team can promptly detect if there is an increase in workload, which could cause severe resource strain or performance degradation.
Log Monitoring and Hybrid Cloud Infrastructure Security
Hybrid cloud infrastructures have emerged as powerful tools for organizations aiming to experience the scalability of public clouds and easy control of private cloud services.
However, while this mix provides much-needed flexibility, it presents unique security challenges. These include visibility gaps that make it difficult for businesses to monitor user activities, detect threats, and ensure compliance.
An organization can employ various measures to address these challenges and prevent data breaches. However, log monitoring has proven to be a crucial tool that provides a detailed account of all events happening within a hybrid cloud infrastructure.
Businesses can gain a holistic view of their cloud environments through continuous analysis of user actions, network activity, and system changes.
The Role of Log Monitoring in Securing Hybrid Cloud Infrastructure
Adding log monitoring to a cloud strategy allows an organization to transform complex and fragmented infrastructure into a secure and inclusive system. This transformation has various benefits, enabling businesses to optimize their performance and prevent internal or external attacks.
Here are five key ways log monitoring helps secure hybrid cloud infrastructures.
Enhancing Visibility Across Environments
Hybrid cloud environments often consist of public and private clouds that meet on on-premise systems. The blend comes with complexities that make it difficult for organizations to maintain clear visibility of all activities and data flows.
Employing log monitoring solutions addresses this issue by aggregating digital records from diverse sources and presenting them in a centralized dashboard. IT teams can monitor all activities across the entire infrastructure without checking individual sources.
Log monitoring makes it easy to identify patterns in user activity that would otherwise be overlooked in a fragmented system. For example, administrators can track users’ movement from accessing a private cloud database to modifying a public cloud application. Through this high-level transparency, an organization can promptly detect and address security vulnerabilities before attacks.
Enabling Early Threat Detection
One of the most critical roles of log monitoring is detecting potential security threats early. Cybercriminals often leave subtle traces of their activities, such as unusual login attempts, unexpected system modifications, or spikes in data traffic.
Log monitoring tools collect and analyze these patterns in real time, enabling businesses to identify and mitigate threats before they escalate.
Examples include brute force attacks, where cyber criminals attempt to gain forceful access by repeatedly guessing login details.
Here, log monitoring tools can identify the threats through multiple failed attempts and give real-time alerts. Similarly, a sudden change in data transfer volume could indicate a potential data exfiltration attempt. Through their predefined rules and machine learning algorithms, log monitoring tools can immediately collect and send threats to security teams to act.
Ensuring Regulatory and Auditing Compliance
Regulatory compliance is a top priority for organizations handling sensitive data. For instance, bodies such as GDPR require data companies to have detailed auditing of all activities and user interactions that happen on their systems.
Log monitoring services are crucial tools that ensure organizations adhere to this compliance requirement by providing a record of all activities within a cloud environment.
Making a readily available record of all digital activities also enables regulatory frameworks to identify and rectify non-compliant activities quickly.
Log monitoring solutions can also generate compliance-specific reports that simplify auditing. This is made possible by giving valuable insights into who accessed which data and how it was used. The company can provide detailed reports to prove adherence to privacy standards during auditing.
Promoting Incident Response and Forensic
Logs are indispensable in understanding the nature and scope of any security breach. These tools provide detailed records of all actions before, during, and after security incidents.
The information then assists security teams in identifying the root cause of the issue and implementing security measures that can prevent recurrence. As a result, an organization can have a well-defined system that allows fast incidents and forensics in the future.
Security incident response is always a race against time. Fortunately, log monitoring tools accelerate this process by providing instant access to relevant data. They also provide critical evidence in legal and regulatory proceedings, enabling organizations to prove their claims.
For example, after an attack, log analysis can reveal that the attackers exploited an unpatched vulnerability in a cloud application. IT experts can use this information to patch the system and refine their security protocols, preventing further exploitation.
Enhancing Proactive Risk Management and Team Collaboration
Log monitoring is essential in creating a proactive approach against security breaches and ensuring the system remains resilient against emerging risks.
For instance, IT teams can quickly identify vulnerabilities, misconfigurations, and outdated software through regular log reviews before they are exploited. Addressing these issues on time minimizes the risk of compromise and heightens overall security posture.
A reliable log management system allows team members to work from a single dashboard. For instance, security experts can collaborate and share insights easily through email alerts and notifications.
This will enable them to analyze and troubleshoot problems within the system quickly. The system can also be essential in onboarding, where it helps run criminal records checks for businesses before hiring.
Best Practices for Log Monitoring in Securing Hybrid Cloud Infrastructure
Adopting log monitoring solutions can enable businesses to enjoy the above benefits faster and improve their security and performance.
However, maximizing the benefits and realizing a return on investment requires organizations to implement certain practices that ensure the solution works well with the existing systems.
Below are six best practices for effective log monitoring in securing a hybrid cloud setup.
Centralize Log Management
Centralizing log management is the primary strategy to create more effective cloud environments. In a hybrid cloud setup, data is generated from multiple sources.
These include private servers, cloud-based applications, and third-party services. Without a central platform, managing and analyzing this data can be challenging. With centralized log management, organizations can enjoy:
- Improved visibility where security teams can have a unified view of all system activities regardless of their sources.
- Efficient correlation where teams can easily relate events from different environments to identify suspicious patterns or anomalies.
- Simplified compliance by ensuring all log information is readily available and auditable.
Automate Analysis
Manual log analysis is no longer reliable in collecting and analyzing massive data generated in a hybrid cloud infrastructure. Automating the process ensures logs are quickly extracted, processed, and analyzed to give meaningful insights.
It also enhances accuracy and scalability by allowing businesses to increase the data they can process without the risks of human error or additional workforce. To effectively automate the process, organizations can:
- Use artificial intelligence log analysis tools that utilize machine learning to detect unusual user behaviors and predict potential threats.
- Incorporate Security Information and Event Management solutions to consolidate security alerts and streamline responses.
- Configure automated workflows to flag high-risk events or escalate them for further actions.
Implement Real-Time Alerts
Speed is a critical aspect in today’s threatened online space. Implementing real-time alerts ensures that security teams are immediately notified of malicious activities. This enables timely response, preventing potential breaches or further damages.
For example, through immediate alerts, security experts can proactively safeguard the infrastructure, such as blocking suspicious IPs or shutting down compromised systems. Some real-time alert implementation tips include:
- Using context-aware alerts that consider user behavior and historical data to prevent false positives.
- Directing alerts to multiple channels, such as emails, SMSs, or dedicated dashboards, to ensure prompt notification.
- Setting up threshold-based alerts for critical events such as multiple failed login attempts or unauthorized access to sensitive resources.
Prioritize Log Retention
Log retention plays a crucial role in creating a robust security posture. Keeping logs for a sufficient period ensures the company can investigate incidents throughout and meet compliance standards.
It also allows for the identification of recurring patterns or emerging threats. To ensure effective log retention, an organization can:
- Define its retention policies based on its needs and compliance requirements
- Use tiered storage systems to balance costs and accessibility
Conduct Regular Audits and Updates
Even the best log monitoring system requires regular maintenance to remain effective. Conducting regular updates and audits ensures the infrastructure adapts to new threats and evolving cloud environments.
It also helps security teams to identify gaps or misconfigurations that occur after using the system for extended periods. This improves efficiency by reducing false positives and uncovering redundant logs. Some implementation tips include:
- Scheduling quarterly or bi-annually audits
- Using audit results to refine log collection policies, alert thresholds, and analysis algorithms.
- Staying up-to-date with the latest best practices and threat intelligence to enhance monitoring capabilities.
Ensure Data Encryption
Securing data is as vital as monitoring it. Logs often have sensitive information, such as user credentials or system configurations. Without property security measures, the information can reach the wrong hands and be exploited.
Through data encryption, businesses can enjoy high-level data integrity, confidentiality, and compliance. To achieve this, data companies can:
- Encryption protocols such as Transport Layer Security are used when transmitting data over the network.
- Implement access controls to restrict who can view or decrypt logs, ensuring only authorized individuals have access.
- Encrypt Stored logs using strong algorithms
Challenges of Log Monitoring in Hybrid Cloud Security
Log monitoring is essential in detecting and mitigating potential security threats within a hybrid cloud infrastructure. However, the solution opens the system to more challenges that can hinder its performance.
Here are four key challenges that can negatively impact the effectiveness of log monitoring software.
1. Privacy concerns: Hybrid clouds often have massive and sensitive data. This complicates compliance with privacy regulations if data traverses different environments.
2. Diverse data formats: Logs from different systems, platforms, and vendors arrive in various formats. These make it difficult for log monitoring solutions to consolidate and analyze data effectively.
3. False positives: These occur when harmless or well-intentioned activities are flagged as potential security threats. They often arise due to noise in data, inconsistent baselines, and complex interdependencies.
4. Older data silos: Many organizations operate with systems that are not well-suited for modern hybrid cloud setups. These can lead to older data silos, often characterized by incompatible formats, fragmented data, and limited visibility.
Conclusion
Log monitoring is an essential pillar of any hybrid cloud infrastructure. It provides comprehensive visibility, early threat detection, and compliance with regulatory frameworks.
However, while these allow organizations to respond to threats and prevent security breaches, the solutions face several challenges. These include privacy concerns, false positives, large data volumes, and older data silos.
To maximize log monitoring effectiveness, businesses can implement best practices such as centralizing log management, automating analysis, and ensuring data encryption.
Selecting the proper monitoring solution also provides a company can have a robust security posture to face any potential threats. As cyber-attacks continue to evolve, it is time for organizations and IT teams to invest in advanced log monitoring tools and strategies that can safeguard their cloud infrastructure effectively.