Key security considerations when implementing DevOps practices include ensuring secure code development, using automation for security testing, implementing strict access controls, monitoring for security vulnerabilities in real-time, enforcing security policies, and fostering a security-conscious culture within the DevOps team.
Today, more than 61% of organizations use DevOps in software development. The demand for DevOps has tremendously increased over the years and is expected to grow further.
By combining development (Dev) and operations (Ops), DevOps has improved collaboration and accelerated the software development by incorporating automation and other practices.
However, security is another crucial aspect one cannot miss out on when building and delivering these applications.
Cyberattacks and threats are increasing with technology advancements. Hence, looking for loopholes in systems and processes involved in developing these applications is crucial to avoid security issues.
This process of testing applications and incorporating security measures into the DevOps process is called DevOps Security.
This blog will discuss DevOps Security in detail, highlighting its importance, key practices, core components, and challenges.
Further, we have noted a few best practices and tools organizations must adopt to reduce security issues.
What is DevOps Security?
DevOps Security is about integrating security measures into your application and software development process to avoid sensitive data leaks and vulnerability risks.
DevOps methodologies cannot track licensing issues, handle password exposure, and perform other security tests.
This is why a separate security team emphasizes implementing automated tools to run vulnerability scans and perform security checks to protect your code and application deployment.
This practice focuses on keeping your software secure at every step of the development life cycle (SDLC).
The central concept of implementing DevOps security practice into your workflow is to secure the continuous integration and continuous delivery (CI/CD) pipeline.
Why is DevOps Security Important?
As per 2024 cybersecurity statistics, 72% of vulnerabilities were traced due to coding flaws.
Cyber threats are constantly increasing, so it has become essential for companies to run internal cybersecurity assessments and security checks to avoid expensive data breaches.
Here are a few more reasons why it is crucial to incorporate DevOps Security practices into DevOps workflow:
Faster development cycles and potential vulnerabilities
Automation has helped companies develop and deploy software and applications rapidly. But at the same time, it has increased the chances of security vulnerabilities.
With faster development, companies often miss minor loopholes, leaving apps and software vulnerable to threats. Hence, it is important to perform automated security testing and real-time monitoring.
Growing cyber threats and risks
The digital world is constantly evolving, as are cybercriminals’ strategies to navigate your systems and software. Cyber threats are becoming trickier and more frequent.
Launching your application without security measures can increase the risk of exposing sensitive data and systems to malicious actors.
Ensuring compliance and reducing risk
For each organization and industry, compliance management and risk reduction are important. It helps companies avoid penalties and reputational damage.
Remember, when software is designed with compliance, companies save a lot from expensive changes and future fixes. Hence, blending compliance into the DevOps process can reduce your security risks.
Proactive security measures
Integrating proactive security into DevOps can reduce the excess time and cost companies invest in fixing vulnerabilities.
Thus, it improves security posture and keeps customer data safe from threats.
Key Practices of DevOps Security
Some of the key practices of DevOps Security are:
Security Testing and Vulnerability Scanning
Early detection in software development and deployment processes can prevent reputational damage and customer trust.
Here are a few methods that can help identify vulnerabilities in applications early.
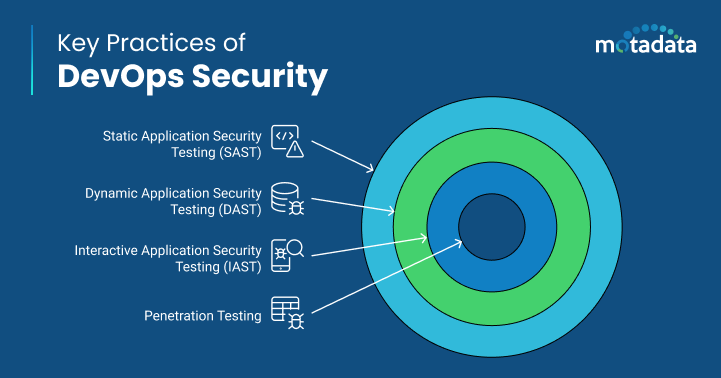
- Static Application Security Testing (SAST) – Static Application Security Testing (SAST) helps analyze code for vulnerabilities without executing the code. SQL injection and insecure APIs can be easily detected using this method.
- Dynamic Application Security Testing (DAST) – Dynamic Application Security Testing (DAST) scans running applications to identify vulnerabilities and find issues like cross-site scripting (XSS) and authentication flaws. A reliable DAST scanner is essential for accurately detecting these security weaknesses in real-time environments.
- Interactive Application Security Testing (IAST) – IAST combines two popular techniques, i.e., SAST and DAST, that help test live applications. This method allows organizations to identify vulnerabilities in real-time as the application runs.
- Penetration Testing – This method simulates attacks to identify potential vulnerabilities in applications and infrastructure.
Secure Coding Practices
Secure coding practices are another key practice of DevOps security. Adhering to code standards and rules helps to avoid common vulnerabilities.
Organizations can use different tools and frameworks for code analysis. Further, developers who receive secure coding training are better prepared to produce robust, safe code.
Secret Management
Protecting sensitive information such as API keys, passwords, and tokens requires safe secret management.
Best practices include avoiding hardcoding secrets in code or configuration files and leveraging environment variables for secure storage.
You can even secure your data using HashiCorp Vault and AWS Secrets Manager.
Further, role-based access controls should be implemented to prevent only authorized users from accessing secrets. For teams seeking to strengthen access controls and reduce risks of credential exposure, using tools like the Bitdefender password generator ensures unique, complex passwords for protecting sensitive DevOps environments.
Infrastructure Security
Configuring safe infrastructure involves adhering to Infrastructure as Code (IaC) principles to guarantee that configurations comply with best practices, such as deactivating unused ports and services.
Firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and network segmentation are all examples of network security methods that improve defense against potential threats.
Incident Response and Recovery
Creating a comprehensive incident response plan with explicit methods for detecting, mitigating, and recovering from occurrences enables teams to respond successfully.
Further, security audits and penetration tests should be regularly run to maintain a solid security posture. These practices allow organizations to identify vulnerabilities and ensure compliance.
What are the core components of DevOps Security?
Here are a few key components essential for creating a strong DevOps Security framework, as this will help the developers at the nascent stage of being a DevOps developer to understand the realm better.
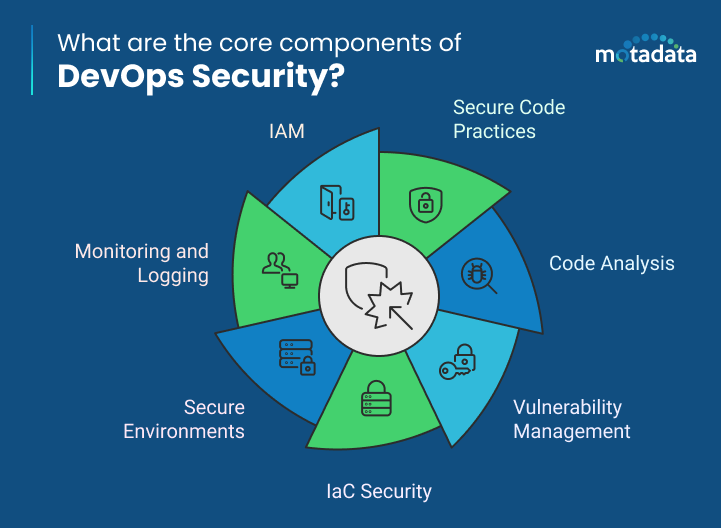
Secure Code Practices
Ensure the code is free from vulnerabilities by providing your developers with proper education and training on common issues like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Companies can improve their security posture with the appropriate knowledge, rigorous review, and testing.
Static and Dynamic Code Analysis
Automated static and dynamic analysis tools are used to check the code for known weaknesses and lousy coding habits early.
Adding SAST and DAST to the CI/CD pipeline prevents security concerns from reaching production.
Vulnerability Management
Regularly scan and patch vulnerabilities to help reduce exposure to threats by initially discovering weaknesses in applications, networks, and infrastructure.
A good vulnerability management program can help minimize security risks and prevent attackers from taking advantage.
Infrastructure as Code (IaC) Security
Secure the Infrastructure as Code (IAC) process to ensure consistent and secure configurations across environments.
Companies ensure that security precautions are implemented by treating infrastructure as code. This strategy contributes to the infrastructure’s long-term security and stability.
Managing secure environments
Operations management is essential to limit risks and prevent unauthorized access. Also, managing privileges carefully and authorizing users only to have access to what they need is vital.
Monitoring and Logging
Implementing monitoring practices helps track what’s happening within the systems and identify suspicious activities in real-time.
Further, logging helps identify flaws and patterns after a security incident. Monitoring and logging data makes it faster to detect and respond to threats.
Identity and Access Management (IAM)
Restrict access based on roles and manage secrets effectively to reduce the risk of unauthorized access.
Incorporating Identity and Access Management (IAM) Solution helps manage user identities better and prevents random users from accessing data without permission. Thus, bit locks security breaches and keeps data safe.
What Are Some DevOps Security Challenges?
Implementing DevOps Security practice is essential, but it also comes with various challenges, including:
Resistance to cultural change
Smooth-shifting from old security practices to a new DevSecOps culture requires support from all team members.
A few employees in your organization might be comfortable with old practices and refuse the adoption of a new culture that values shared responsibility and open talks.
The resistance to cultural change can slow down the process essential for successful DevOps Security.
Balancing speed and security
Another challenge that most organizations face is creating a balance between speed and security.
The fast DevOps processes can result in neglecting minor security problems, resulting in future data breaches.
Hence, companies must adopt practices that guarantee regular security checks without slowing development cycles.
Skill gaps in security knowledge
Security is one of the essential elements of the software development process.
If any member of the developers and operations teams lacks the necessary expertise to address security issues, it may create loopholes in code and increase the risk of security threats.
Hence, ensuring that there is no skill gap in security knowledge among development and operations teams is necessary.
Managing security in cloud-native environments
Unlike on-premises systems, cloud-native environments have various components that demand secure setup management, data safety, etc., to maintain customers’ trust.
However, there can be multiple challenges related to container security and issues securing multi-cloud configurations.
Weak Access Controls
Without proper access controls and identity management systems, people might gain unauthorized access to critical systems and cause data breaches.
Unauthorized users can further compromise customer’s sensitive data and cause reputational damage.
Lack of DevOps fundamentals
Organizations lacking an understanding of the basic DevOps practices may struggle to integrate security effectively.
Incorporating security practices can be challenging without a strong knowledge of DevOps fundamentals and ideas such as automation, continuous improvement, etc.
What are DevOps Security Best Practices?
Tackle the above-listed challenges and ensure successful DevSecOps in the workflow requires the adaption of these few best practices:
Automating security at every stage of the pipeline
Incorporate automated security tools to identify and address CI/CD pipeline vulnerabilities.
Automatically running vulnerability scans and performing code analysis during the building and development can prevent security risks and reduce human error.
Further, security tests conducted during the development process can prevent delays.
Conducting regular security audits and testing
Frequently run audits and maintain logs with restricted access. Running security audits and security tests regularly will help keep your software up-to-date.
You can find weaknesses in real time and fix vulnerabilities before anyone takes advantage of them. You can run scans or perform penetration testing to identify and resolve potential security issues early.
Integrating security tools into CI/CD pipelines
Several security tools like SonarQube and OWASP ZAP are available in the market that you can integrate into the CI/CD pipeline to automate security checks.
Securing your CI/CD pipeline from the beginning of the project and code creation can prevent things from going in the wrong direction.
Further, it will help keep security at the forefront throughout the software development lifecycle.
Training teams to prioritize security
Remember, it is not only the duty of special security teams to ensure safety at all levels but also the entire DevSecOps team. Hence, regular training for security practices is a must for all members.
This will help fill the skill gap and train members for various topics, including threat modeling, configuration management, vulnerability management, incident response, etc.
Thus making sure all team members understand and prioritize security in their workflows.
Turn DevOps into DevSecOps
Handling security issues requires a complete shift from DevOps to DevSecOps. The practice involves adding new tools to the process and how development teams think about security.
From planning to designing and deployment, security checks, and tests must be performed simultaneously.
There must be a proper collaboration between development, operations, and security teams to protect the software from the beginning.
DevOps Security Tools and Technologies
Security has become a top priority in the software development process. Here are a few tools and technologies to make the process easier and handle complex issues.
- Popular DevOps security tools: SonarQube for code quality and security analysis, OWASP ZAP for web application scanning, and Burp Suite, a penetration testing tool to validate application security during staging.
- Cloud security tools: For cloud-native applications and services, it is best to invest in AWS Security Hub for centralized security management of the AWS environment, Azure Security Center for Azure resources, and Google Cloud Security Command Center (SCC) to get a consolidated view of security risks and compliance violations for Google Cloud resources.
- Container security tools: To secure containers, go for Aqua Security, which protects the entire lifecycle of containers, Twistlock (Prisma Cloud) for secure deployments, and Kubernetes-native tools for security within Kubernetes environments.
Future Trends in DevOps Security
With technology advancements, we are noticing quick changes in security trends. Organizations may adopt a few future trends to handle complex threats and secure data.
Rise of AI-driven security automation
AI-powered tools are increasingly used to detect and respond to threats in real-time. Intelligent systems with artificial intelligence and machine learning are expected to change how security tasks are managed and performed.
Thus, it makes it easier for big corporations to handle complex and high-volume threats efficiently.
Focus on Zero Trust architecture
Zero Trust principles ensure strict access controls and continuous validation of users and devices. Many companies support remote work, and managing security with old practices is insufficient.
Using Zero Trust principles, companies can get a strong security posture and prevent unauthorized users or attackers from moving freely within the network.
Growing adoption of Secure Access Service Edge (SASE)
SASE integrates networking and security to provide secure access to applications from anywhere.
By combining security and network services, SASE simplifies operations and improves security posture in cloud environments.
Enhanced collaboration between DevOps and SecOps teams
Improved collaboration fosters a unified approach to building and securing applications.
This shift will help develop a culture of shared responsibility and fill the gaps between DevOps and SecOps teams, thus helping organizations attain goals faster and build customer trust.
How Motadata Can Help You with DevOps Security
Motadata provides an AI-powered DevOps monitoring tool for organizations demanding total security and compliance in software development.
With this powerful tool, organizations can secure DevOps workflow and precisely control who can access data and improve product quality.
Further, it comes with broad monitoring capabilities and health checks for your configuration management systems and container orchestration platforms.
With Motadata, you can maintain a strong security posture without delays. Try the free trial to get quality results and improve productivity.
FAQs:
DevOps emphasizes the integration of development and operations teams to increase productivity, whereas DevSecOps integrates security into the DevOps lifecycle, making it a shared responsibility.
Monitoring and logging provide real-time insights into potential threats and track if rules are followed. They help spot unusual activity and security problems quickly and enable real-time response to security incidents.
DevOps focuses on speed and agility, which might increase vulnerabilities. On the other hand, DevOps Security reduces these risks by incorporating security at each pipeline level.
DevSecOps transforms security from a separate function to an integrated part of the DevOps process. It ensures ongoing security testing while performing development tasks and creating a culture of shared responsibility.