As modern IT infrastructure becomes increasingly complex, businesses generate massive amounts of logs compared to the past in real time.
Therefore, streamlining this unstructured log data into a more structured form becomes vital with this growing complexity.
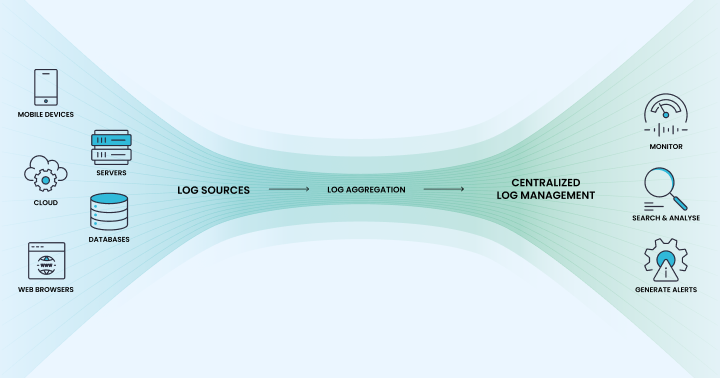
Organizations must collect unstructured log data from various sources, extract meaning from them, and store them in a centralized repository.
That’s where Log Aggregation comes in. Log Aggregation is like gathering all the pieces of a puzzle and placing them together to form a complete picture
Let us take a deep dive into the intricacies of log aggregation, its working, challenges, benefits, and more
What is Log Aggregation?
Log aggregation identifies log sources, collects data, and consolidates the logs at a central location.
From the perspective of modern IT infrastructure, Log aggregation is crucial to bringing structure into unstructured raw log data, enabling logs as a medium for multiple use cases, such as efficient infrastructure and performance monitoring, troubleshooting, analysis, and even identification of security issues.
For instance, an e-commerce platform can use log aggregation to monitor user activity, a financial institution can aggregate logs from firewalls, antivirus software, and other applications to detect potential security breaches, and a SaaS platform can identify potential performance issues by aggregating logs from its web servers, application servers, and databases.
How Log Aggregation Works?
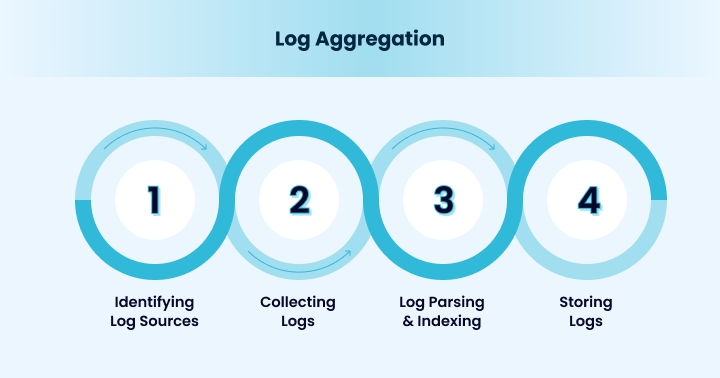
There are several steps involved in aggregating logs into a central repository, which can be described as follows:
1. Identifying Log Sources: Modern Infrastructure has a diverse range of logs. As a first step, it is vital to identify the different sources you need to aggregate the logs for analysis.
2. Collecting Logs: Logs can be collected from various sources, such as applications, databases, network devices, web servers, OSs, and more, using methods such as file ingestion, Syslog, or automated pipelines.
3. Log Parsing & Indexing: After the logs are collected, they must be parsed to gain meaningful insights. Parsing the raw log data helps to transform unstructured data into valuable information. The logs are then indexed to make their log search and retrieval easy.
4. Storing Logs: The parsed logs are then consolidated and stored at a central location to facilitate retrieval and enable further analysis and log management.
You can also use a unified platform such as Motadata AIOps, which can perform all the necessary log aggregation steps and much more by directly accessing log sources, ingesting logs from diverse sources, parsing and aggregating them into a central location for log management & analysis.
Getting Started with Log Aggregation
To reap the benefits of Log Aggregation, it is vital to identify the log sources and set up your environment by choosing the right log aggregation tool. Let us look into how to do that.
Identifying Your Log Sources
As previously discussed, the first step to log aggregation is identifying the log sources crucial to your organization.
The log sources in your infrastructure could be your Servers, Applications, and Networks.
Since there is a diverse range of components in modern-day infrastructure, it is vital to identify all the pieces of the puzzle that make up the crucial logs for your infrastructure.
What are the Tools and Resources Needed for Effective Log Aggregation?
Once you identify the various log files and event logs to be ingested and aggregated, it is important to choose the right log management tool for log collection, aggregation, parsing, storage, and maybe even comprehensive log monitoring and management.
For effective log aggregation, you’ll need the following:
- Log aggregation tools collect, process, and store log data.
- Log storage: A centralized repository to store aggregated logs. This could be a dedicated log management platform or object storage.
- Infrastructure: Network infrastructure to connect log sources to the aggregation tool.
- Personnel: IT professionals with the skills to implement and manage the log aggregation system.
We will now discuss the right tool that serves all the above purposes and provides much more in a unified console.
Why Log Aggregation Matters?
Log Aggregation is more than just a technical necessity. It’s a strategic approach that yields significant benefits:
1. Streamlining and Standardizing Logs:
Log aggregation reduces complexity by streamlining log management, consolidating logs from various sources with different formats, and standardizing them into a common format.
This is crucial because it eliminates differences between different formats, making searching, retrieving, and analyzing logs easier.
2. Enhancing System Performance through Insights:
Aggregated log data enables administrators to gain valuable insights into performance issues and resource utilization in system and application performance.
3. Improving Security Posture:
Log aggregation enables organizations to improve their security posture by actively monitoring and identifying potential threats and malicious activities using their infrastructure logs consolidated from various sources, including Servers, Applications, and Firewalls.
4. Log Management, Monitoring, and Analysis:
Log Aggregation enables a unified approach to log management by enabling platforms to collect, aggregate, store, monitor, and analyze the logs from a centralized location. Effective log management and monitoring enable organizations to make data-driven decisions to support their businesses.
5. Efficient Troubleshooting and Resolving Incidents in Production:
Aggregated logs enable quick identification and resolution of incidents by allowing a holistic view of system operations. Engineers can easily access and analyze the logs to pinpoint the root cause and provide a swift resolution.
By implementing log aggregation, organizations can significantly improve the efficiency, security, and reliability of their IT infrastructure, making it an essential component of modern IT strategies.
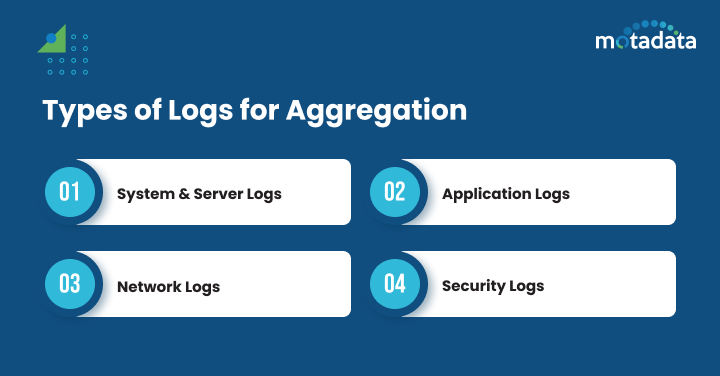
Types of Logs for Aggregation
Logs can be categorized into various types, such as system, application logs, security, and network logs. The logs offer different insights based on their type. Let us look into the types of logs below:
- System and Server Logs include valuable information about server and operating system events. They are useful for monitoring OS performance and diagnosing potential hardware issues.
- Application Logs include application-specific events and errors. They are useful for monitoring application performance and behavior and improving user experience.
- Network Logs: These provide details about network traffic patterns and help identify bandwidth and connectivity issues
- Security Logs : provide details about security events. They are crucial for identifying unauthorized user access and security breaches.
Challenges and Considerations
Log Aggregation has its own set of challenges, including managing large volumes of data, dealing with the complexity of the data structures of the diverse range of logs, and ensuring data privacy.
1. Log Volumes:
One significant challenge in log aggregation is managing the large volumes of logs in modern infrastructure. As organizations scale, the sheer volume of log data grows exponentially, making it difficult to collect, store, and analyze it.
2. Log Data Complexity:
Aggregating logs from diverse sources can be challenging. The logs are generated in different formats, which require parsing them to align them in the same format. This can lead to increased overhead for organizations.
3. Log Data Privacy and Security:
Log data can sometimes be sensitive and entail strict regulatory and compliance requirements, as they pose privacy and security concerns. It is vital to ensure that the logs are securely stored, transmitted, and accessed for analysis to ensure data privacy and security.
Best practices for overcoming these challenges
1. Managing Log Data:
Log management tools with data retention policies are important to handle the challenge of large volumes of log data. Regularly archive or delete logs to manage storage costs and performance by configuring an apt retention period.
2. Log Data Standardization:
Use consistent log formats and normalization techniques to simplify the data after log aggregation.
3. Ensuring Log Data security:
Encrypting log data both in transit and at rest to protect sensitive data is vital. Implement strict access controls and an audit trail to monitor log data and ensure compliance requirements.
4. Scalability:
Choose a scalable aggregation tool that fits the growing organization’s needs. This ensures the infrastructure can handle additional load as the log volume increases.
Choosing the Right Log Aggregation Tool
Imagine a unified platform that solves multiple use cases of log management and provides a comprehensive and efficient approach to managing your log data so that you get the most out of the bucks you spend.
That’s what you are looking for, isn’t it? We’ll discuss that soon, but first, let’s look at what you should expect from the log management tool you choose.
1. Unified Console:
An all-in-one platform for collecting, parsing, analyzing, and visualizing the log data from multiple sources. This ensures simplified monitoring, higher efficiency, comprehensive insights, and more in one place.
2. Out-of-the-Box Log Parsing Support:
The tool should be able to parse the logs belonging to a diverse range of infrastructure, including network devices, applications, and servers from all the major vendors prevalent in the industry.
3. Threat Detection using Logs:
Tools that can detect security threats using ingested logs and send out an alert have an edge over tools that can’t.
4. Log Correlation:
Some tools can detect the correlated events with the help of the ingested logs. This helps to identify the surrounding events that led to the event you are analyzing and also helps to identify the repercussions of the same event effortlessly.
5. Live Log Tailing:
Some tools enable real-time viewing and analyzing the ingested logs. This enables administrators to detect and troubleshoot issues as they occur and view crucial activity in your infrastructure.
6. Comprehensive Log Analytics:
Some tools equip you with an out-of-the-box tool to analyze the logs by creating widgets to visualize the log data and generate meaningful insights.
7. User Interface:
A user-friendly interface is crucial for efficiently analyzing log data. Look for features like intuitive dashboards, customizable alerts, and powerful log search capabilities.
With Motadata AIOps, it’s time to look beyond mere Log Aggregation tools with all the above features and more via its unified console. From Log collection, Dynamic Log parsing, Log Storing, Advanced Log management & analytics to business-driven insights, you can fulfill all your needs at one destination.
Utilizing automatic Out-of-the-box dynamic parsing, Motadata AIOps transforms and standardizes logs from diverse sources to ensure sophisticated and effortless analysis.
Regular threat detection ensures robust security mechanisms. Leverage advanced features such as Log Correlation and live Log Tailing to understand your infrastructure logs comprehensively.
To top it all off, equip yourself with the intuitive Log Explorer to ensure your logs are intelligently categorized for easy search and retrieval.
Create widgets to visualize log data from various sources, including applications, servers, and network devices, to gain critical insights into infrastructure and help relevant teams quickly identify why a performance issue occurred.
Conclusion
To summarize, we explored what log aggregation is, its benefits, its challenges, and how to choose the right log aggregation tool. We discussed how to log aggregation software centralizes log entries from various sources, enhances monitoring, aids troubleshooting in production environments, and more.
Efficient log analysis and management are crucial in maintaining system integrity, optimizing performance, and ensuring a robust security posture for modern businesses. In today’s data-oriented world, log aggregation is vital.
It allows organizations to gain comprehensive insights into their IT environments and quickly respond to incidents in the production environment.
Don’t limit yourself to log aggregation tools, but expand your capabilities with a unified tool like Motadata AIOps that provides immense value.
Improve your log analysis and monitoring capabilities. Start aggregating your logs today and unlock the full potential of your log data with Motadata AIOps.
FAQs
Log aggregation is crucial for identifying and diagnosing issues in IT systems, improving security, and enhancing operational efficiency by providing a comprehensive view of system activities.
The key benefits include improved troubleshooting, enhanced security monitoring, faster incident response, better compliance, and more effective resource management.
Log aggregation enhances security by providing real-time insights into system activities, detecting anomalies, and helping to identify potential security threats early.