Network Devices enabled with the Simplified Network Management Protocol (SNMP) send out different types of SNMP messages.
SNMP Traps are one such category of message formats among the many types comprising information regarding alerts and critical problems.
SNMP Traps are instrumental in managing network infrastructure since they provide crucial information that can impact performance, availability, and overall health.
This article will explore each aspect of SNMP Traps and Trap Management so that you can make more informed decisions and take appropriate actions.
What is SNMP Trap Management?
SNMP trap management involves receiving and processing automated alerts generated by network devices.
These alerts, known as SNMP traps, provide valuable information to network administrators about critical events like hardware failures, network outages, or security breaches.
Organizations can proactively address issues, minimize downtime, and optimize network performance by effectively managing these alerts.
Effective SNMP trap configuration involves monitoring and responding to important events on a single request, such as device overheating, to ensure the smooth operation of a network.
- Configuring devices to send traps: Ensuring network devices are configured to generate traps for specific events.
- Collecting traps: Using a network management software (NMS) to receive and process incoming traps.
- Analyzing trap data: Correlating trap information with other network data to identify root causes and potential issues.
- Triggering actions: Automating responses to critical traps, such as sending notifications or initiating troubleshooting procedures.
Organizations can proactively address network issues, improve uptime, and enhance overall performance by effectively managing SNMP traps.
What is the Importance of SNMP Trap Management?
SNMP traps are crucial for proactive network management.
They provide real-time alerts about critical events, allowing administrators to respond to issues before they escalate swiftly.
Organizations can significantly reduce downtime, improve network performance, and ensure system reliability by effectively managing SNMP traps.
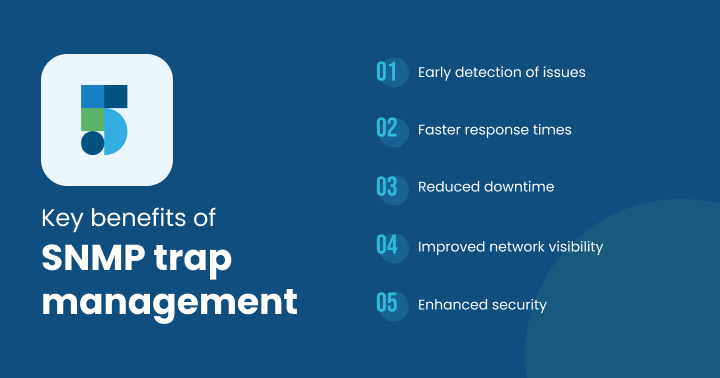
Key benefits of SNMP trap management include:
- Early detection of issues: Proactive identification of potential problems.
- Faster response times: Quick reaction to critical events.
- Reduced downtime: Minimization of network disruptions and service outages.
- Improved network visibility: A deeper understanding of network health and performance.
- Enhanced security: Detection of potential security breaches through trap analysis.
Challenges in SNMP Trap Management
Managing SNMP traps effectively can present several challenges:
- Trap Volume: Many traps can overwhelm the management system, challenging prioritizing and analyzing critical events.
- Trap Standardization: Variations in trap formats and content across different devices can hinder consistent analysis and correlation.
- False Positives: Unnecessary traps can generate alerts, leading to alert fatigue and reduced efficiency.
- Trap Filtering: Efficiently filtering traps based on severity, source, or content can be complex.
- Trap Correlation: Relating multiple traps to identify underlying issues requires sophisticated analysis capabilities.
- Security: Ensuring the security of traps is crucial to prevent unauthorized access and tampering.
- Trap Management Tools: Selecting and configuring appropriate tools for trap management can be challenging.
Addressing these challenges is essential for maximizing the benefits of SNMP trap monitoring and maintaining network resilience.
Let’s dive a bit deeper and understand the mechanism of how SNMP Trap messages work.
Understanding SNMP Traps
SNMP Trap is one of the five categories of messages supported by the SNMP protocol.
It comprises crucial information about the event that occurred, the device’s identity, time of occurrence, severity, and the nature of the issue.
All the other messages in the SNMP protocol require the management software to request data from the network devices at periodic intervals actively.
The device only relays the data when the software asks it to.
On the flip side, SNMP Trap messages are unsolicited messages sent to the management software if a critical event is triggered.
The software never fetches SNMP Trap messages, which are always sent by the device itself.
How Does SNMP Trap Work?
Simple Network Management Protocol) is a widely used for monitoring and managing network devices.
It facilitates communication between network management system (NMS) and managed devices (like routers, switches, and servers).
Key Components:
- Manager: The central control point that collects and analyzes network data.
- Agent: Software on managed devices that gathers information and sends it to the manager.
- Managed Devices: Network devices are being monitored and managed.
Operations:
- Get: The manager requests specific information from an agent.
- Set: The manager can modify configuration settings on a managed device.
- SNMP Trap: The agent proactively sends the manager alerts (traps) about critical events.
SNMP is a cornerstone of network management, providing essential data for monitoring network health, troubleshooting issues, and optimizing performance.
Types of SNMP Traps
There are two categories of SNMP Traps, Generic and Enterprise-Specific.
Generic SNMP Traps
The Internet Engineering Task Force (IETF) has predefined and standardized generic traps, which are commonly used to report general events or conditions that may occur on network devices.
These are six generic traps defined in the SNMP protocol:
- Cold start trap: This trap signal is sent when the device is turned on and restarted from a completely powered-off state. This indicates that the device’s configuration might have been reset to factory defaults.
- Warm start-up: Indicates a device restart without configuration loss, often due to software/firmware updates or routine maintenance.
- Link down trap: A Link Down trap indicates a loss of network connectivity for a previously active network interface. This event often signifies a physical layer issue, such as a disconnected cable or network hardware failure.
- Link-up trap: A Link-Up trap signals the restoration of network connectivity for a previously inactive network interface. This event indicates that a previously reported network connection issue has been resolved.
- Authentication failure trap: This trap indicates a failed authentication attempt on the device. This event may signal potential security breaches or unauthorized access.
- EGP neighbor loss trap: This notification indicates that a router has lost communication with a neighboring router in an Exterior Gateway Protocol (EGP) network. This disruption in the routing protocol can potentially lead to changes in the routing table, affecting network connectivity and routing paths. It’s essential to investigate this trap to identify the root cause of the neighbor loss and take corrective actions to restore normal network operation.
Enterprise-Specific SNMP Traps
Enterprise-specific traps are custom alert messages that device manufacturers or network administrators define to signal specific device or network events.
These highly granular notifications cater to an organization’s unique monitoring needs.
Below are some examples:
- CPU utilization trap: Triggered when a device’s CPU usage surpasses a predefined limit, indicating potential performance bottlenecks or resource exhaustion.
- Memory Utilization: This is generated when a device’s memory consumption surpasses a predefined threshold. Insufficient memory can lead to system slowdowns, application crashes, or even unexpected shutdowns, indicating a potential risk to the device’s stability and overall performance.
- Power supply failure trap: This indicates a critical hardware issue in which the device’s power supply unit has malfunctioned or failed, requiring immediate attention.
- Temperature trap: This alert is generated when a device’s operating temperature surpasses safe thresholds, potentially leading to hardware damage or system malfunctions. It signals a critical condition requiring immediate attention.
- Interface status change trap: This trap indicates a change in the operational state of a network interface. It could be a transition from an active (up) state to an inactive (down) state or vice versa, potentially impacting network connectivity and communication.
- RAID Failure Trap: This trap indicates a critical failure within a Redundant Array of Independent Disks (RAID) system, potentially compromising data integrity and availability. It signals the need for immediate attention to prevent data loss or system instability.
Enterprise-specific traps offer tailored monitoring, allowing organizations to define custom alerts based on their unique network and device configurations.
This flexibility ensures granular oversight aligned with specific business needs.
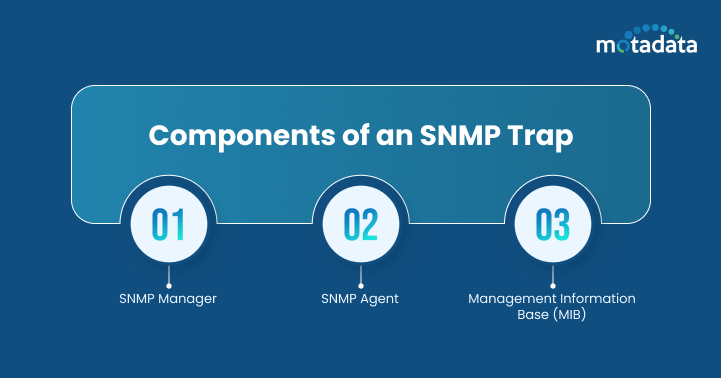
Components of an SNMP Trap
SNMP Trap operates on SNMP Protocols, and the SNMP Protocols require 3 crucial components to function.
Below is a gist for each of these components that will shed light on their roles and functionalities:
1. SNMP Manager:
An SNMP Manager is an application or system that actively fetches and processes SNMP Traps from network devices.
It acts as a central manager that handles the network’s monitoring and management points.
2. SNMP Agent:
The SNMP Agent is the on-device module that facilitates the collection of device information.
The agent continuously monitors the device’s status, performance, and other operational parameters.
When a critical event occurs that meets the criteria for sending an SNMP Trap, the agent generates the Trap message and sends it to the SNMP Manager.
3. Management Information Base (MIB):
SNMP Traps use Object Identifiers (OID) to identify a specific event or error. OID is unique for each event and device.
MIB is a database that contains information regarding each device, IP addresses, status, and performance along with the OIDs.
It acts as a central dictionary and helps the manager to understand the meaning of a Trap message.
Best Practices for SNMP Trap Management
1. Trap Configuration
Defining Critical Events
Critical events are specific occurrences within a network or device that warrant immediate attention.
These events often signify potential issues or failures that can disrupt network operations.
Administrators must carefully identify these critical events when configuring SNMP traps to ensure that only the most important alerts are generated.
This prevents alert fatigue and allows for focused troubleshooting.
Examples of critical events include:
- Device failures (hardware or software)
- Network outages or connectivity issues
- Security breaches or unauthorized access attempts
- Resource exhaustion (CPU, memory, disk)
- Configuration errors or changes
2. Filtering Unnecessary Traps
It’s crucial to filter out irrelevant or low-priority alerts to manage SNMP traps effectively.
Organizations can reduce alert fatigue and focus on critical events by implementing robust filtering mechanisms.
Filtering can be based on criteria such as trap severity, device type, or specific event types.
For instance, filtering out redundant information, such as informational traps or those from less critical devices, can significantly improve alert efficiency.
Properly configured filters help prioritize alerts, promptly addressing essential notifications while minimizing distractions from less critical events.
3. Trap Severity Levels
Trap severity levels categorize the importance of an alert generated by a managed device.
This hierarchical classification aids in prioritizing responses and filtering less critical notifications.
Common severity levels include:
- Critical: Indicates a severe event that requires immediate attention, such as a complete system failure or data loss.
- Major: Represents a significant event impacting system performance or availability but not causing a complete outage.
- Warning: Signals a potential issue or degradation in service that requires monitoring.
- Informational: Provides non-critical updates or status changes for informational purposes.
By assigning appropriate severity levels to traps, network administrators can effectively manage alert volumes and focus on promptly addressing high-priority issues.
4. Trap Frequency
Trap frequency refers to the rate at which a device generates SNMP traps.
Configuring trap frequency judiciously is essential to avoid overwhelming the management system with excessive notifications.
- High-frequency traps: Suitable for critical events requiring immediate attention, such as hardware failures or security breaches.
- Low-frequency traps: Appropriate for less critical events or informational updates.
Administrators can carefully set trap frequencies to optimize the balance between timely alerts and manageable alert volume.
Trap Reception and Processing
Choosing the Right SNMP Management System
Selecting the appropriate SNMP management system is crucial for effective network monitoring and management.
Several factors should be considered when making this decision:
- Scalability: The system should handle many devices and data points without compromising performance.
- Performance: The system should efficiently collect and process SNMP data to provide real-time insights.
- Features: Essential features include device discovery, performance monitoring, fault management, configuration management, and security.
- SNMP Versions: Ensure compatibility with the SNMP versions used by your network devices (v1, v2c, v3).
- Alerting and Notification: Effective alert mechanisms, including email and SMS, are crucial.
- Reporting and Visualization: Robust reporting and visualization capabilities allow for data analysis and trend identification.
- Integration: Compatibility with other network management tools and systems is essential for a holistic approach.
- User Interface: A user-friendly interface enhances usability and productivity.
- Security: Strong security features, such as authentication and encryption, are vital to protect sensitive network data.
- Cost: Evaluate the pricing model and overall cost of ownership, including licensing, maintenance, and support.
Motadata AIOps simplifies SNMP Trap Management by efficiently collecting, analyzing, and responding to critical network alerts.
By leveraging advanced analytics and automation, Motadata empowers organizations to proactively address issues, optimize network performance, and minimize downtime.
Efficient Trap Handling
Effective SNMP trap handling is crucial for maintaining network health and performance.
Key considerations for efficient trap reception and processing include:
- High-Performance Trap Receivers: Employing specialized hardware or software to handle many traps without performance degradation.
- Load Balancing: Distributing trap processing across multiple servers to prevent bottlenecks.
- Security: Implementing robust security measures to protect against unauthorized access and tampering with trap data.
Correlation of Traps with Other Data Sources
Correlating SNMP traps with other data sources is crucial for effective root cause analysis and incident resolution.
By combining information from multiple sources, network administrators can gain deeper insights into network behaviour and identify underlying issues.
Key data sources for correlation include:
- Performance metrics: Correlating traps with performance metrics (CPU utilization, memory usage, disk I/O) can help identify resource constraints that might be causing issues.
- Configuration data: Comparing trap data with device configurations can help determine if misconfigurations contribute to problems.
- Log data: Analysing log messages alongside traps can provide detailed information about the events leading to an alert.
- Inventory data: Knowing a device’s hardware and software components can aid in troubleshooting.
- Geographic information: Correlating traps with device location can help identify regional issues or patterns.
Motadata AIOps enhances trap analysis by correlating SNMP traps with diverse data sources.
This comprehensive approach integrates performance metrics, configuration data, log information, inventory details, and geographic location to provide deeper insights into network behavior.
By identifying patterns and relationships between these data points, Motadata AIOps empowers network administrators to pinpoint root causes and resolve issues efficiently and accurately.
Trap Analysis and Response
Real-Time Monitoring and Alerting
Real-time monitoring and alerting are essential components of effective SNMP trap management.
Organizations can minimize downtime and mitigate potential issues by rapidly detecting and responding to critical events.
Key elements of real-time monitoring and alerting include:
- Low-latency trap reception: Ensuring minimal delay in receiving SNMP traps from managed devices.
- Instantaneous correlation: Correlating incoming traps with other data sources for rapid analysis.
- Real-time visualization: Displaying trap data and system health metrics in real-time dashboards.
- Timely alerts: Generating immediate notifications for critical events via various channels (email, SMS, push notifications).
- Automated response: Triggering predefined actions based on trap severity and content.
- Escalation procedures: Defining escalation paths for unresolved alerts to ensure timely attention.
By implementing these elements, organizations can achieve high network visibility and responsiveness, enabling them to proactively address issues and maintain optimal network performance.
Root Cause Analysis
Root Cause Analysis (RCA) is critical to effective SNMP trap management.
By delving deeper than the initial symptoms, RCA helps identify the underlying cause of a problem, enabling corrective actions to prevent recurrence.
Key steps in RCA for SNMP traps:
- Data Correlation: Combining trap data with other network metrics, logs, and configuration information to establish relationships.
- Pattern Recognition: Identifying recurring patterns in trap data to pinpoint potential issues.
- Time-Series Analysis: Examining trap data over time to detect trends or anomalies.
- Impact Assessment: Evaluating the potential consequences of the identified root cause.
- Corrective Action Planning: Developing strategies to address the root cause and prevent future occurrences.
By systematically applying RCA to SNMP trap data, organizations can significantly improve network reliability, optimize performance, and reduce downtime.
Read Also: How to Use Monitoring Tools to Improve Root Cause Analysis
Automation and Orchestration
Automation and orchestration are essential for efficient SNMP trap management.
Organizations can significantly improve response times and reduce human error by automating routine tasks and integrating multiple systems.
Key areas of automation and orchestration include:
- Trap Classification: Automatically categorizing traps based on severity, source, and content.
- Ticket Generation: Automatically creating incident tickets in ITSM systems for critical traps.
- Notification: Sending alerts to appropriate personnel via email, SMS, or other channels.
- Remediation Actions: Automating routine remediation tasks, such as restarting services or rebooting devices.
- Root Cause Analysis: Leveraging automation to correlate trap data with other IT systems for in-depth analysis.
- Workflow Orchestration: Coordinating multiple actions and systems based on trap information.
Organizations can optimize their response to SNMP traps by implementing automation and orchestration, reduce manual intervention, and improve overall network resilience.
Trap Security
SNMP V3 Encryption
SNMPv3 is the most secure version of SNMP, offering encryption and authentication to protect data that is trapped during transmission.
Unlike its predecessors, SNMPv3 employs advanced security mechanisms to ensure data confidentiality, integrity, and authenticity.
Key security features of SNMPv3 include:
- Authentication: Verifies the identity of both the sender and receiver of the SNMP message, preventing unauthorized access.
- Privacy: Encrypts the SNMP message content, protecting sensitive information from eavesdropping.
- Integrity: Ensures that the SNMP message has not been tampered with during transmission.
By leveraging SNMPv3, organizations can significantly enhance the security of their SNMP trap communications, safeguarding critical network information from unauthorized access and modification.
Access Control Lists
Access Control Lists (ACLs) are essential for securing SNMP trap communications.
Network administrators can control which devices or management systems can send or receive SNMP traps by implementing ACLs.
This helps prevent unauthorized access and protects sensitive network information.
Key functions of ACLs in SNMP trap security:
- Trap Destination Control: Specifies which management systems can receive traps from a device.
- Trap Source Verification: Ensures that traps originate from authorized devices.
- Community String Validation: Verifies the authenticity of SNMP messages using community strings.
- Access Control: Restricts access to SNMP management functions based on user roles and permissions.
By effectively utilizing ACLs, organizations can significantly enhance the security of their SNMP environment and protect against unauthorized access and malicious activities.
Trap Filtering and validation
Trap filtering involves selectively accepting or rejecting traps based on various criteria, such as:
- Source IP address: Limiting traps to specific devices or network segments.
- Trap type: Filtering based on the type of event or condition reported by the trap.
- Trap severity: Prioritizing critical traps while discarding less important ones.
- Trap content: Examining trap data for specific keywords or patterns to determine relevance.
By implementing effective trap filtering, organizations can significantly reduce the volume of irrelevant traps, improving the efficiency of trap management and analysis.
Trap validation ensures the authenticity and integrity of received trap messages.
Key validation steps include:
- Source verification: Confirming that the trap originates from a trusted device or network segment.
- Message integrity: Checking for any modifications or tampering with the trap data.
- Community string validation: Verifying the validity of the SNMP community string used for authentication.
- Trap format validation: Ensuring that the trap message adheres to the SNMP standard.
Through rigorous trap validation, organizations can mitigate the risk of malicious attacks and ensure the accuracy of trap data.
By combining trap filtering and validation, organizations can establish a robust defense against unauthorized access and malicious activities, protecting their network infrastructure and sensitive information.
Conclusion
Effective SNMP trap management is essential for maintaining a healthy and responsive network infrastructure.
Organizations can significantly reduce downtime, improve network performance, and optimize resource utilization by proactively identifying and addressing network issues through timely analysis and response to SNMP traps.
Recap of Best Practices
Effective SNMP trap management is crucial for maintaining a healthy and responsive network infrastructure.
To achieve this, organizations should focus on the following key areas:
- Trap Configuration: Carefully define critical events, implement robust filtering, assign appropriate severity levels, and control trap frequency.
- Trap Reception and Processing: To efficiently handle incoming traps, utilize high-performance trap receivers, load balancing, and security measures.
- Trap Analysis and Response: Correlate traps with other data sources, perform root cause analysis, and implement real-time monitoring and alerting.
- Trap Security: Employ SNMPv3 for encryption and authentication, implement access control lists, and validate trap authenticity and integrity.
By following these best practices, organizations can optimize their SNMP trap management processes, reduce alert fatigue, and improve overall network performance.
Importance of Ongoing SNMP Trap Management
Ongoing SNMP trap management is critical for maintaining optimal network performance and availability.
By continuously monitoring and analysing trap data, organizations can:
- Identify emerging issues: Proactively detect potential problems before they escalate into major outages.
- Optimize network resources: Adjust system configurations based on trap data to improve resource utilization.
- Enhance security: Detect and respond to security threats promptly.
- Improve service quality: Ensure optimal network performance for end-users.
- Support compliance: Demonstrate adherence to regulatory requirements through effective trap management.
- Facilitate capacity planning: Utilize trap data to predict future network needs and resource allocation.
In essence, ongoing trap management serves as a proactive approach to network health, enabling organizations to make data-driven decisions and prevent costly disruptions.
Future Trends in SNMP Trap Management
While SNMP remains a cornerstone of network management, the landscape is evolving.
Several trends are shaping the future of SNMP trap management:
- Integration with Telemetry: As network devices generate vast amounts of data, integrating SNMP traps with telemetry-based solutions can provide a richer context for analysis. This combination will enable more in-depth troubleshooting and performance optimization.
- AI and Machine Learning: Advanced analytics powered by AI and ML can be applied to SNMP trap data to identify patterns, predict anomalies, and automate response actions.
- Cloud-Based Trap Management: Cloud-based platforms can offer scalable and cost-effective solutions for handling large volumes of SNMP traps, providing centralized management and analysis capabilities.
- Enhanced Security: As threats evolve, stronger security measures will be essential for SNMP trap management, including advanced encryption, authentication, and authorization mechanisms.
- Standardization and Interoperability: Increased standardization of SNMP trap formats and content will improve compatibility and interoperability between different management systems.
- Correlation with IT Operations Data: Integrating SNMP traps with other IT data sources (e.g., IT Service Management, log management) will enable a more holistic view of the IT environment.
By embracing these trends, organizations can optimize their SNMP trap management practices, gain deeper insights into network performance, and improve overall IT operations.
FAQs:
SNMP traps are unsolicited messages sent by network devices to notify management systems of significant events, such as failures or status changes.
Effective trap management ensures timely detection of issues and helps network administrators respond quickly to critical events.
Yes, traps can help detect issues before they escalate, allowing proactive actions based on predefined conditions.
By enabling quick response to alerts and preventing small issues from becoming major incidents, trap management helps maintain high network availability.