We live in a connected world, where managing network configuration is very important for all organizations. The new age business organizations must have a competent network configuration manager so as to ensure maximum uptime.
This blog is the ultimate guide to network configuration management system (NCM). In addition, it provides details why network configuration and change management matters, its main parts, best practices, and what the future holds.
With network management configuration, businesses can have better control and can also make change management easier.
Understanding Network Configuration Management (NCM)
Network Configuration Management (NCM) covers how we manage and control the settings of network devices. This includes tasks like managing changes in configurations, discovering devices, and using configuration templates.
A key part of network configuration management software is making sure the network meets industry standards and security rules.
Network administrators use configuration management in network management tools to make tasks easier, lower human error, and keep the network running smoothly. Moreover, knowing about performance and configuration management is important for improving network performance and reducing mistakes.
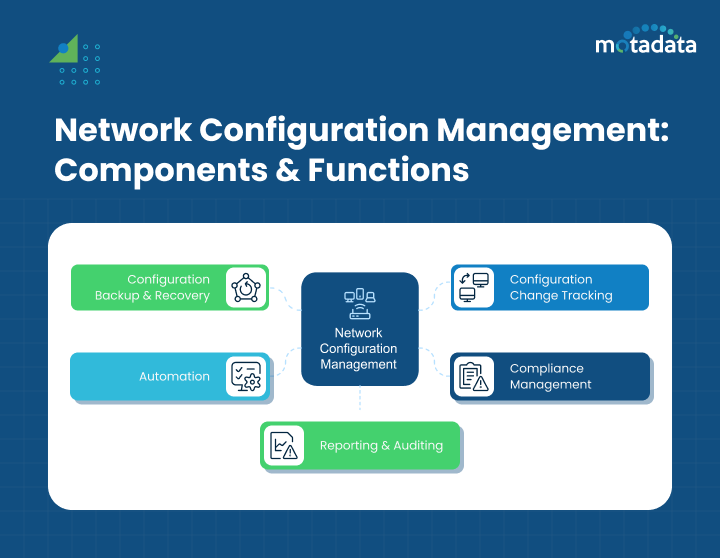
Key Components of NCM
At its heart, NCM has important parts that come together to give you a complete solution for network setup and management. These parts help keep your network configuration safe and secure.
They include configuration backup and recovery. This feature protects you from data loss and helps you recover quickly during disasters. There is also configuration change tracking, which lets organizations keep an eye on changes and check them. This helps boost security and supports troubleshooting.
Configuration Backup and Recovery
Configuration backups act like a safety net. They help quickly restore network devices to a good state if something goes wrong, like during failures or disasters. Making regular backups is important for keeping a business running smoothly and reducing downtime.
Backups are important for network config change management because they protect the quality of data. By making copies of these settings regularly, companies keep a history that can be used to get everything back on track after unexpected events.
Storing backups in one place and keeping them secure is key for network configuration management (NCM). This ensures that sensitive information is easy to reach and well-protected.
Configuration Change Tracking
Tracking configuration changes is important for keeping a stable network. It helps improve security and makes sure businesses follow industry standards. NCM tools make this easier. They provide clear logs that show who made changes, when they were made, and where in the network these changes happened.
Real-time monitoring of configuration changes helps organizations spot and handle unauthorized changes quickly. This reduces the risk of possible threats or disruptions. By setting clear rules for change management and using NCM tools to stick to them, companies can lower the risks that come with changes.
Having a strong change management system, which often works with NCM tools, makes it easier to get approvals and send notifications. It also provides options for rolling back changes. This helps to ensure that network infrastructure modifications are controlled and approved.
Compliance Management
Being in line with industry standards and rules is very important for organizations. It helps ensure data security, maintain good security practices, and avoid legal issues. NCM tools help make compliance management easier by automating audits and creating reports.
When businesses set up compliance policies in NCM tools, they can monitor their network devices all the time. This checks whether they meet necessary requirements, like those in HIPAA, PCI DSS, or SOX. This active way of managing compliance helps organizations quickly find and fix problems or mistakes.
Doing regular compliance audits and creating reports gives important information about the network’s overall security. This helps in making smart choices and shows that they follow regulatory rules.
Automation
Network automation is an important part of good Network Change Management (NCM). It helps organizations make repetitive tasks easier, cut down on human errors, and boost overall efficiency. When IT teams automate tasks like configuration backups and software updates, they can save time and use their resources for more important projects.
Automating complex network operations helps save time and decrease mistakes. It also keeps the configurations consistent and accurate. This is especially important in large networks, where doing things by hand can take a lot of time and lead to errors.
Good automation strategies use scripting languages or NCM tools. These help create workflows that automate certain configuration tasks or react to specific events.
Reporting and Auditing
Regular audits are important for keeping networks healthy, safe, and compliant. NCM tools provide strong reporting and auditing features. They give clear information about changes in configurations, compliance status, and possible vulnerabilities.
Detailed reports on device inventory, configuration changes, and user activity help network administrators find and fix problems early, which improves network security.
Also, NCM tools usually work with vulnerability management systems. They link configuration data with known vulnerabilities. This lets you see all network security risks clearly.
The Role of NCM in Network Lifecycle Management
NCM is important for the whole life of the network. This includes everything from setting up devices to managing them over time and even taking them out of service. NCM provides a single place to manage configuration data. This makes network operations smoother and lowers the chances of mistakes or discrepancies.
When new devices are added, NCM tools help keep configurations consistent. This reduces the chance of errors. Also, when old equipment is retired, NCM processes help ensure that devices are removed safely. This lowers security risks and keeps the network steady.
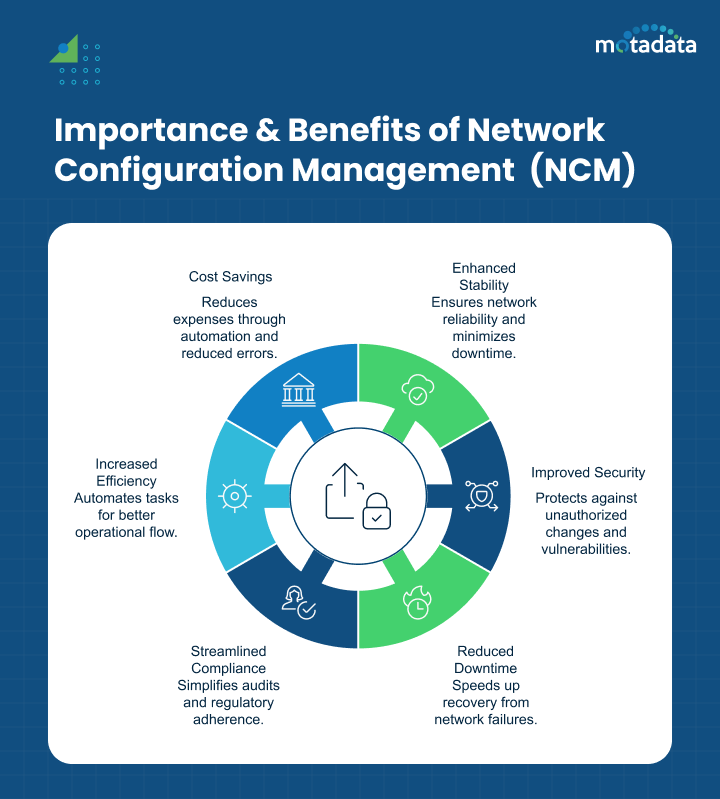
The Importance and Benefits of NCM
In today’s fast-changing tech world, businesses need strong network infrastructure. NCM is not just a good idea; it is essential for companies that want a secure, reliable, and efficient network.
NCM is important because it helps solve many problems in network management. It offers a clear and automated way to manage configuration data. This reduces the chance of human error and keeps things consistent across the network.
1. Enhanced Network Stability and Reliability
A good NCM strategy helps make networks more stable and reliable. When organizations keep their configurations accurate and consistent, they can avoid problems like outages or slowdowns caused by errors in setup.
Configuration errors can often lead to network downtime. NCM tools help cut down on these errors. They provide a single source of truth for configuration data, which helps make sure everything is consistent across devices.
Also, NCM helps with change management. It allows network administrators to test and check configurations before using them in the live network. This makes it less likely to have unexpected issues.
2. Improved Security Posture
NCM is essential for organizations that want to improve their network security. It helps by constantly checking for changes in configurations. NCM tools can find and alert admins about any unauthorized changes that might signal a security issue.
Also, NCM helps enforce security rules throughout the network. By setting and applying standard configurations, companies can make sure that security best practices are applied on all devices.
NCM solutions include features for managing vulnerabilities. These features show security weaknesses tied to software versions. This way, organizations can quickly patch and fix issues to reduce risks.
3. Reduced Downtime and Faster Recovery
Downtime can really hurt an organization’s profits. NCM is crucial for reducing downtime. It helps businesses recover quickly from network failures or disasters.
Regular configuration backups let organizations quickly fix a device if it fails. This helps them get back to normal with little interruption in service.
Also, NCM makes network maintenance tasks easier. It automates things like software upgrades and configuration changes. This saves time and makes the process smoother.
4. Streamlined Compliance and Auditing
To meet industry rules and standards, you need to pay close attention to details and do regular audits. NCM tools make managing compliance much easier. They can automate audits and create detailed reports.
By setting compliance rules in NCM solutions, companies can make sure their network devices follow important regulations like HIPAA or PCI DSS. This way of managing compliance helps reduce the chances of facing expensive fines or legal issues.
NCM also offers a central place to store configuration data. This makes audits easier and helps companies show their compliance quickly.
5. Increased Operational Efficiency
NCM greatly boosts efficiency by automating everyday tasks. It makes complex network operations easier and gives centralized control over network settings. This makes it possible for IT teams to spend their time on more important projects.
With automation for tasks like backing up configurations, updating software, and enforcing policies, network administrators can save time and energy that they would otherwise use for manual work.
Easier workflows and automated routines help solve network problems faster, improving operational efficiency and lessening the effects of disruptions on business.
6. Cost Savings
Using a strong NCM strategy with a good configuration management tool helps organizations save money. It can cut down on downtime and errors. It also helps make compliance easier. This way, businesses can spend less on IT and get more from their investments.
Many NCM tools let organizations try them for free. This helps them see if the tool fits their needs before buying it. The trial time allows them to check the features and how well it works with their current systems.
Also, the automation features of NCM tools save a lot on labor costs. This is because they reduce the need for manual setup and management tasks.
NCM Processes and Best Practices
Implementing good NCM processes and following best practices are important for getting the most out of network configuration management. These practices help manage configurations in a clear way. They ensure that everything is consistent, secure, and efficient.
A key best practice is to create a complete configuration baseline. This baseline is a reference for any future changes. It helps quickly spot and fix any differences from the expected state.
1. Configuration Baseline Establishment
Establishing a configuration baseline means writing down the best settings for all network device configurations in the IT environment. This baseline acts as a gold standard. It helps compare and check any future changes.
Using configuration templates is a smart choice when setting up this baseline. Templates make sure everything is uniform and lower the chances of making mistakes. They offer ready-made settings that can be applied to many devices easily. This saves time and improves the accuracy of configurations.
It’s also important to regularly review and update the configuration baseline. This helps it stay in line with changing security policies, the best practices in the industry, and changing business needs.
2. Change Management Procedures
Implementing a clear change management process is important for keeping track of changes made to the network configuration. This organized way of managing changes helps lower the chance of unauthorized or wrong changes that could hurt network operations or security.
Good change management involves several steps. First, you need to document the proposed change. Then, you have to get the necessary approvals. Next, test the change in a safe setting. After that, schedule when to put it in place, and finally, document what happens afterwards.
Using NCM tools to manage configuration changes in one place gives a full audit trail. This makes troubleshooting easier and helps keep track of any changes made to device configurations.
3. Automation Strategies
Automation is very important for making NCM processes more efficient and reducing human error. When IT teams automate boring and repetitive configuration tasks, they can save time and focus on bigger, more important projects.
It is vital to make sure that automation strategies fit the needs and goals of the organization. Tasks like configuration backups, software updates, and policy enforcement should be automated because they take a lot of time and can have mistakes when done manually.
Choosing the right tools and technologies for automation is key to getting it right. NCM tools usually have built-in features for automation, like scripting languages and workflow engines. This helps in setting up automated configuration tasks easily.
4. Regular Audits and Compliance Checks
Regular audits and compliance checks are very important. They help to make sure that network devices follow security policies, industry standards, and rules. NCM tools make this easier by automating audits and creating detailed reports.
These audits can spot problems like configuration changes that are different from the baseline, unauthorized changes, or any security weaknesses. By regularly checking network compliance, companies can fix issues before they become serious. This helps them avoid costly fines or legal problems.
Using NCM together with security information and event management (SIEM) or other security monitoring tools makes the organization’s security even stronger. It does this by connecting configuration data with security events.
5. Disaster Recovery Planning
A strong disaster recovery plan is very important for any organization. NCM helps to quickly restore network services if a disaster happens. Configuration backups are a key part of this plan. They allow for fast recovery of network infrastructure.
It is important to regularly test the disaster recovery plan. This checks if it works and helps make updates if needed. The testing should include restoring configuration backups to ensure they are good and complete.
By using NCM best practices and regularly updating the disaster recovery plan, organizations can reduce downtime. This helps keep things running smoothly during unexpected problems.
NCM Tools and Technologies
There are many NCM tools and technologies that can help organizations manage their network settings better. These tools offer different features, like automatic configuration backups, tracking changes, checking for compliance, and enforcing policies.
When choosing an NCM tool, it’s important to think about network size, complexity, security needs, and how well it can work with your current IT setup. The best NCM solutions have easy-to-use interfaces, in-depth reports, and strong automation features that make network management easier.
Implementing NCM: A Step-by-Step Approach
Implementing NCM doesn’t need to be hard. If organizations use a clear plan, they can start to add NCM ideas and best practices into their network management.
The first step is to look at your current network configuration. You should find areas that need improvement and set clear goals for NCM implementation. This first step shows a path to create a successful NCM program.
Assess Your Current Network Configuration
Evaluating your organization’s network configuration is the first step for good NCM. This assessment helps you find current setups, possible problems, and places to get better.
Start by making a complete list of your network devices. This list should include detailed information about each device, like device type, vendor, model, operating system, IP address management details, and other important information.
Next, look at any existing network documentation that you have. This information can give you useful details about the network’s design, security rules, and any past changes to the setup.
Define Your NCM Goals and Objectives
Setting clear goals and objectives is very important for a successful NCM implementation. Creating goals that are specific, measurable, achievable, relevant, and time-bound (SMART) helps everyone understand the plan, and it’s easier to track progress.
Think about your organization’s business goals and how better network management fits into those goals. Decide on the range of the NCM implementation. This could mean covering the entire network or focusing on areas that need improvement.
For example, your goals could be to improve network security, comply with industry standards, reduce network downtime, or increase efficiency by using automation.
Select the Right NCM Tool
Picking the right network configuration management tool is very important for your NCM efforts. You need a tool that fits your network needs and works well with your current IT setup.
When looking at different NCM tools, think about their features, how well they can grow, how easy they are to use, the support from the vendor, and their cost. Make sure to find key features like device discovery, backup and recovery for configurations, real-time change tracking, compliance reports, and automation options.
Focus on tools that have strong security features. Role-based access control and configuration encryption are good examples to help keep your important network configuration data safe.
Develop and Document NCM Policies and Procedures
Creating clear NCM policies and procedures is very important. This helps keep network operations consistent and standardized. These guidelines should cover all parts of NCM. This includes configuration backups, change management, compliance monitoring, and disaster recovery.
You should write detailed policies for configuration backups. These policies should mention how often to back up, how long to keep backups, and where to store them. Make sure to explain how to start backups, check they are correct, and restore configurations when needed.
Next, document the change management procedures. This should outline who is responsible, what approvals are needed, and how to test configuration changes. It’s a good idea to use configuration templates. This helps keep things standard and minimizes the chance for mistakes.
Train Your IT Staff
Investing in proper training for your IT staff is important. This helps to implement and manage your NCM program successfully. Trained staff can use NCM tools well. They can follow the rules and solve problems that come up.
The training should include different parts of NCM. This includes network device discovery, inventory management, configuration backup and recovery, change management processes, and compliance monitoring.
It is also helpful to build a culture of sharing knowledge and learning in your IT team. This will help everyone adopt the best practices for NCM.
Implement and Monitor NCM Processes
With your NCM policies, procedures, and trained staff ready, you can start using the NCM processes. This means you will use the NCM tool you selected and set it up to meet your needs. You should also connect it to your current network infrastructure.
Begin by slowly starting NCM on a few devices or network segments. This will help you test the processes and spot any issues before you fully roll it out.
Keep a close eye on how well your NCM processes work. Use the reporting and auditing tools that come with your NCM tool. Make sure to check configuration compliance, change logs, and other important metrics. This way, you can find areas to improve and make sure your NCM program achieves its goals.
Continuous Improvement and Optimization
NCM is not just something you do once. It is a process that needs ongoing improvement and adjustment. As your network grows and changes, your NCM strategies and processes should change too.
Make sure to regularly check and update your NCM policies and procedures. This will help you adapt to changing business needs, new technologies, and rising security threats. You should also ask for input from IT staff who manage the network to find out where you can improve.
If you notice any configuration drift—when device settings change from what was originally planned—fix it quickly. Use the version control and rollback features in your NCM tool. This will help you go back to a previous good setting and figure out what caused the drift.
Challenges and Considerations in NCM
Creating and keeping a strong NCM strategy can be hard. Organizations often face pushback from IT staff who are used to manual setups. To overcome this, it’s important to communicate, offer training, and show the advantages of NCM.
Another difficulty is managing old devices that do not work with new NCM processes or have few automation options. In these situations, you might need to look for other solutions or think about updating old equipment.
Dealing with Legacy Devices
Legacy devices can create special challenges for NCM. They have limited abilities, old technology, and often don’t support new management protocols. But it’s important to keep these devices in mind when planning your NCM strategy.
If possible, think about upgrading legacy devices to newer ones. They often provide better support for NCM protocols and automation features. Look into ways to replace them slowly to avoid disrupting your network operations.
For devices that can’t be upgraded or replaced right away, look for other solutions. You could use terminal emulators or custom scripts to get configuration data and add it to your NCM tool.
Scaling NCM for Large Networks
As networks get bigger, the tasks of managing their setups become harder. To adjust NCM for larger networks, you need to plan carefully. You also need the right tools and smooth processes to keep everything running well.
Use automation features to make tasks easier. This includes things like finding devices, backing up configurations, and checking for compliance on many devices. Choose NCM tools that have strong automation options. They should work well even as your network grows without slowing down.
Think about using a layered NCM system. This means managing configurations at different levels, like by region, department, or type of device. This way makes it simpler to manage and share tasks within a big IT team.
Maintaining Configuration Consistency
Keeping configurations consistent across all network devices is vital. This helps make sure the network is stable, secure, and meets standards. When configurations do not match, it can cause problems like unexpected actions, security risks, and issues with fixing problems.
Having one main source for all network device configurations is very important. This central place, usually found in the NCM tool, allows all configuration changes to be recorded, tracked, and easy to find.
Make sure to use configuration templates a lot. They help enforce standard setups for similar devices or groups of devices. Templates have a set of settings that can easily be used across many devices. This practice lowers the chances of errors that come from setting things up by hand.
Securing NCM Data and Access
NCM tools hold sensitive network configuration data. Therefore, it is important to keep this data safe and control who can access it. Put in place strong security measures to stop anyone from accessing or changing the NCM data without permission.
Make sure all user accounts in the NCM tool have strong passwords. Use multi-factor authentication, if you can, to further improve security.
Regularly check and update who can access NCM data. Access should follow roles and responsibilities in the IT team. Limit remote access to the NCM tool. Use secure ways to communicate, like SSH or VPN, when accessing data from outside.
Overcoming Resistance to Change
Implementing NCM often requires changes in the organization. Some IT staff may resist these changes because they are used to manual setup methods. To address this resistance, it is important to communicate clearly, provide good training, and show the advantages of NCM.
Explain why NCM is important and how it fits with the organization’s IT service management (ITSM) goals. Highlight the benefits, such as better security, less downtime, more efficiency, and easier compliance.
Make sure to train the IT staff on the selected NCM tools and processes. This will help them gain the knowledge and skills needed to accept these changes. Encourage them to share their thoughts and quickly resolve any concerns to make the transition smoother.
Future Trends in NCM
As technology changes, the area of NCM will change as well. New trends like more network automation, the use of artificial intelligence (AI), and cloud-based NCM solutions will influence how we manage networks in the future.
AI and machine learning will become more important in NCM soon. Tools that use AI can look at network data. They can find problems, predict issues, and automatically fix them. This will help make networks more stable and secure.
Network Automation and Orchestration
Network automation and orchestration are becoming very important in how we manage networks today. They help organizations make their operations smoother, cut down on mistakes, and increase overall efficiency. Automation deals with automating single tasks, while orchestration goes a bit further by automating complete workflows.
When businesses use network automation and orchestration, they can handle many network management tasks. This includes backing up configurations, updating software, checking for compliance, and fixing problems when they arise.
Connecting network management systems with IT automation tools helps organizations create complex workflows. It allows them to automate responses to events or changes in the network.
AI and Machine Learning in NCM
The progress in AI and machine learning is changing many areas of IT, including NCM. AI-powered NCM tools offer smart automation and useful insights for network management. This improves both efficiency and security.
Machine learning algorithms can study past network data. They identify patterns and notice unusual activities. They can also predict problems, which helps IT teams to fix issues before they affect operations.
AI can also take care of complicated network operations. These include network optimization, enforcing security policies, and managing compliance. This allows IT staff to focus on more important projects.
Cloud-Based NCM Solutions
Cloud-based NCM solutions are becoming popular. They help organizations manage their network settings with flexibility, scalability, and cost savings. These solutions come as a service, which means there is no need for hardware or software maintenance on-site.
Cloud-based NCM tools make it easier to manage networks that are spread out across different locations. They provide a single console for control and visibility over the complete IT setup.
Also, these solutions can scale up or down. This allows organizations to change their NCM capabilities as their network expands or their needs change.
Intent-Based Networking (IBN)
Intent-Based Networking (IBN) changes how we manage network configuration. Instead of relying on manual work, IBN lets networks run based on what users want.
It uses automation and machine learning to turn business goals into network rules. IBN makes complex network operations easier. It also improves network performance and lowers human error.
By using IBN, organizations can run their network management more efficiently. They can keep their configurations in check and stop problems before they happen. IBN makes network configuration tasks smoother, boosts security, and gives a faster way to handle network infrastructure.
Conclusion
Mastering Network Configuration Management (NCM) is very important. It helps to improve network stability, security, and efficiency. If businesses use NCM best practices and the right tools, they can cut down on downtime. They can also boost compliance and save money.
Future trends in NCM like network automation, AI integration, and cloud-based solutions will bring even more progress in how we manage networks. By adopting these new ideas, organizations can stay ahead in technology. It is important to stay informed and take action to improve your network management strategies using the power of NCM.
FAQs:
Network configuration management has many benefits. It helps make security better, boosts how efficiently things work, and saves money. NCM keeps the network stable, helps meet rules, and simplifies IT tasks by gathering configuration management in one place.
NCM helps make security better by keeping track of network device configurations. It finds unauthorized changes and spots devices that need security updates. Overall, NCM boosts the security of an organization’s network.
Network configuration is about managing and controlling how devices are set up in a network. It makes sure the devices are arranged correctly and securely. Network management covers much more. It involves monitoring, fixing problems, and improving everything related to network operations.
The goal of network configuration management is to keep the network stable, secure, and clear of issues. This is done by handling network device configurations. It makes sure that devices are set up the right way, that we keep track of changes, and that we meet any rules we need to follow.
Common problems in using NCM are connecting older systems, making solutions fit larger networks, and keeping settings the same across devices. To fix these issues, you often need to use technology tools, improve processes, and manage changes in the organization.