Behind every successful business or organization is a complex web of interconnected systems and applications.
But with complexity comes risk, and managing that risk is critical to ensuring the smooth operation of these systems.
That’s where log management comes in.
Log management provides valuable insights into system performance, security, and other essential metrics by collecting and analyzing logs from across the organization.
Keep reading as we explore the world of log management and discover how it can help businesses and organizations stay ahead of the curve in today’s fast-paced digital landscape.
What is Log Management?
Log management collects, stores, and analyses logs generated by computer systems, applications, and network devices.
It involves consolidating logs from multiple sources, normalizing the data, and then analyzing it to gain insights into system performance, security, and other essential metrics.
This information can be used to troubleshoot issues, identify potential security threats, and optimize system performance.
Effective log management is essential for businesses and organizations to ensure their systems’ smooth operation and meet regulatory requirements. Logging software captures the logs and stores them for future analysis.
Log management can be done in an on-premises or cloud-based environment.
Cloud-based logging has many benefits, such as scalability and cost-effectiveness. It also reduces the need to manage hardware or software upgrades in an on-premises environment.
What are Logs or Log files?
Logs or log files are records of events that occur within a computer system, application, or network device.
These events can include user activity, system errors, security events, and other important information.
Logs are typically stored in text files and contain a timestamp, a description of the event, and further relevant details.
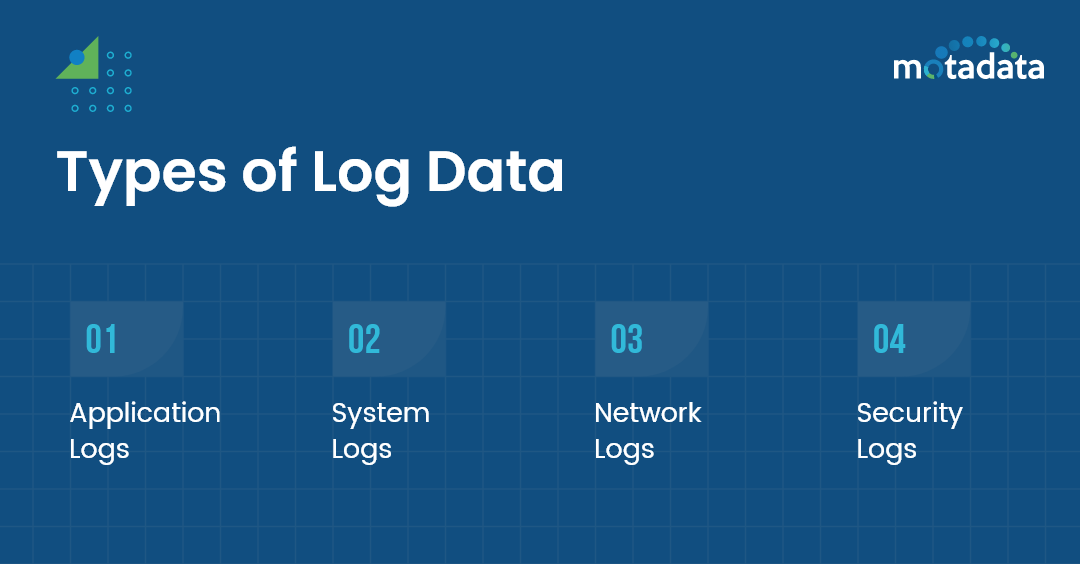
Types of Log Data
There are many different types of log data. The most important types of log data are application, system, network, and security logs. Let us dive deep into each type of log data.
1. Application Logs:
Application logs track what an application does while running on your system. They can be used for debugging purposes or tracking down problems with the application itself. For example, Apache Access Logs can be used to track down the events that occurred in the Apache web server.
2. System Logs:
System logs are derived from Windows Event Logs, which can be used to collect information about the state of your system at a given time (e.g., CPU usage). They can be used to diagnose problems with your operating system or hardware.
3. Network Logs:
Network logs are used to keep track of an individual’s online activity. Syslogs/Linux Syslogs can be used to find out information about the sites that individuals visit, what they search for, and how much time they spend on them.
4. Security Logs:
Security logs are a type of log that records information about a system’s security events. Syslogs such as IDS and IPS can detect unauthorized access attempts, monitor failed login attempts, and detect intrusions.
Take control of your logs and secure your infrastructure with Motadata’s comprehensive log management solution.
Benefits of Log Management
1. Enhanced Security and Threat Detection:
Log management enables the collection, storage, and analysis of logs generated by various systems and applications. By aggregating and analyzing logs, you gain valuable insights into security events, anomalies, and potential threats. These logs can be used to identify and respond to security breaches, detect unauthorized access attempts, and mitigate risks proactively.
2. Efficient Troubleshooting and Issue Resolution:
Log management centralizes logs from multiple sources, allowing a comprehensive view of your system’s activities. When troubleshooting issues, log data can provide valuable clues about the root causes of problems, helping IT teams identify and resolve issues more efficiently. Logs can reveal error messages, warnings, and stack traces, aiding debugging and minimizing downtime.

3. Compliance and Audit Readiness:
Maintaining logs is crucial for compliance with various industry regulations and data protection standards. Log management facilitates the collection, retention, and analysis of logs, ensuring you have the necessary documentation to demonstrate compliance during audits.
By having a well-implemented log management solution, you can track and report on user activities, system changes, and security events, which are often required for regulatory compliance.
4. Performance Monitoring and Optimization:
Log management enables performance monitoring by capturing key performance indicators (KPIs) and metrics from different components of your infrastructure. Analyzing these logs helps you identify performance bottlenecks, resource utilization patterns, and system abnormalities.
With this information, you can proactively optimize your systems, allocate resources more efficiently, and ensure smooth operations.
5. Incident Response:
In the event of a security incident or suspected breach, log management plays a crucial role in forensic investigations. Logs serve as a valuable source of evidence, allowing security teams to reconstruct events, trace the source of an attack, and perform post-incident analysis.
This information is essential for incident response, facilitating timely and effective mitigation strategies.
By implementing a robust log management solution, you can leverage these benefits to strengthen your organization’s security posture, streamline troubleshooting processes, ensure regulatory compliance, optimize performance, and facilitate incident response.
Why does your organization need a log management solution?
A log management solution is indispensable for any organization as it provides crucial visibility into the activities of systems, networks, and applications. Centralizing and analyzing logs enables timely detection of security incidents, aids in troubleshooting and issue resolution, ensures compliance with regulatory requirements, optimizes system performance, and facilitates effective incident response.
Log management is an essential part of maintaining a healthy system. Logs are unstructured data that can provide insights into how a system operates. For instance, if the log contains errors that lead to downtime, it would be possible to discover and resolve the problem before it happens again. Logs can also help identify security breaches and even help with forensics in case of an attack on the system.
A profound and powerful Log Management solution should be able to benefit the organization in the matters such as:
- Unified data storage with centralized log aggregation
- Monitor servers, apps, performance, service availability, and other important metrics
- Monitor entire infrastructure, database, applications in a unified dashboard for faster root cause detection.
- Monitor, troubleshoot, and optimize resources hosted on popular public cloud services like AWS and Azure (supported services include EC2, RDS, S3, Lambda, etc. For AWS and Azure VM, Azure SQL Database, Azure VM, etc. For Azure).
Challenges of Log Management
The massive amount of data, numerous sources, and connected devices challenge IT operations to execute seamlessly. On top of that, the migration to the cloud and increased complexity in the architectures add to the complications.
Here are the common challenges organizations face while approaching Log Management solutions.
Standardization: The log files are helpful for IT professionals and security administrators to effectively analyze the log data and produce insights to make critical business decisions. And this makes it essential, as all the data needs to be in the same format.
Volume: With the vast amount of data, it becomes challenging to collect, analyze and produce actionable information out of them. Considering the various data types, formats and resources, a log management system must be able to manage a large amount of data and provide powerful insights.
Bandwidth: Indexing within the log files can be expensive and cause latency between the incoming data and producing information and search results. Latency causes a dependency on whether the log management system has indexed the data.
Burden: Log management solution does save a lot of time. However, the digital log management solution helps automate a few activities and alleviates the strain on IT professionals.
Best Practices of Log Management
Challenges come with solutions and strategies to tackle them. Here are some key considerations IT professionals should keep an eye on while adopting any log management solution.
Prioritizing Automated Practices: With enormous capacities and possibilities, many processes can be automated. Therefore, it is essential to prioritize the activities and automate them based on their dependencies and systems.
Centralized Data: With all the data in one place, it doesn’t just improve data accessibility but also enhances the organization’s security. The centralized log structure helps reduce the breakout time or the critical window wherein hackers usually move to other parts of the system.
Retention Policy: When a large amount of data is generated, organizations should discern what information is collected and how long it should be retained.
Cloud and Endless Potential: Cloud technologies have added potential and unlimited capabilities for IT enterprises. Organizations should approach a modern cloud-based solution for the log management system as it enhances flexibility and scalability. It also allows organizations to expand or shrink their processing capacities based on the requirements.
Conclusion
Log management plays a vital role in maintaining an organization’s IT infrastructure’s integrity, security, and performance. Log management enables proactive monitoring, efficient troubleshooting, and timely detection of security incidents by collecting, storing, and analyzing logs generated by various systems and applications.
It provides valuable insights into system activities, user behaviour, and potential threats, facilitating effective incident response.
Furthermore, log management supports regulatory compliance, enhances operational efficiency, and helps optimize system performance. By implementing a robust log management solution, organizations can ensure the availability, reliability, and confidentiality of their critical data, ultimately contributing to the overall success and resilience of the business.
Motadata AIOps comes with unified log management and full-stack monitoring solution. A solution that helps organizations execute rapid investigation, troubleshooting, and higher-level analytics. Effortless collection methods unify logs, metrics, and streaming data for a centralized view with deeper context to analyze logs events.
Thus, improving the performance efficiency and enhancing security, making the organization and infrastructure stand strong among the market firm and challenges.